Table of Contents
Introduction to Secure Software Development Life Cycle (SSDLC)
In the ever-evolving landscape of technology, where the digital realm intertwines with almost every aspect of our lives, ensuring the security of software applications has become paramount. Enter Secure Software Development Life Cycle (SSDLC), a methodology designed to integrate security measures at every stage of the software development process. Let’s embark on a journey to unravel the essentials of SSDLC, understanding its significance, components, and implementation strategies.
Understanding SSDLC: Secure Software Development Life Cycle, often abbreviated as SSDLC, is a systematic approach to integrate security practices within the software development process. Unlike traditional software development methods that often tack on security measures as an afterthought, SSDLC prioritizes security from the inception of the project to its deployment and beyond. By ingraining security into each phase of development, SSDLC aims to mitigate vulnerabilities, reduce risks, and fortify software against potential cyber threats.
Components of SSDLC: SSDLC encompasses several key components, each playing a crucial role in ensuring the security of the software throughout its lifecycle:
- Planning and Requirements: At the outset, SSDLC begins with thorough planning and requirements gathering, where security considerations are factored into the project scope. Identifying potential security risks and establishing security requirements lay the foundation for a robust security posture.
- Design: During the design phase, security architecture is crafted alongside the software’s functional design. Security mechanisms such as access controls, encryption, and authentication protocols are integrated into the system design to preemptively address security vulnerabilities.
- Implementation: In the implementation phase, developers translate the design into executable code while adhering to secure coding practices. Techniques like input validation, output encoding, and parameterized queries are employed to mitigate common security pitfalls such as injection attacks and cross-site scripting.
- Testing: Rigorous testing forms a pivotal aspect of SSDLC, encompassing various techniques such as static analysis, dynamic analysis, and penetration testing. These tests help identify vulnerabilities and weaknesses in the software, allowing developers to rectify them before deployment.
- Deployment: Prior to deployment, the software undergoes a final security assessment to ensure it meets the requisite security standards. Secure deployment practices, including secure configuration management and secure installation procedures, are employed to safeguard the software during deployment.
- Maintenance and Updates: Even after deployment, the security journey continues with regular maintenance and updates. Patch management, vulnerability scanning, and security audits are conducted periodically to address emerging threats and fortify the software against evolving security risks.
Implementation Strategies: Implementing SSDLC requires a concerted effort and adherence to best practices. Some key strategies to effectively integrate SSDLC into the software development process include:
- Education and Training: Educating developers about secure coding practices and providing training on security protocols can empower them to proactively address security concerns during development.
- Automated Security Tools: Leveraging automated security tools such as static code analyzers, vulnerability scanners, and intrusion detection systems can streamline the identification and remediation of security vulnerabilities.
- Security by Design: Adopting a ‘security by design’ approach ensures that security considerations are embedded into the software architecture and development process from the outset.
- Continuous Monitoring: Implementing continuous monitoring mechanisms allows organizations to detect and respond to security incidents in real-time, enhancing the overall security posture of the software.
Importance and Benefits of Implementing SSDLC
In the rapidly evolving landscape of cybersecurity, organizations are continually striving to fortify their digital fortresses against an array of threats. Amidst this relentless pursuit of resilience, the Software Security Development Life Cycle (SSDLC) emerges as a beacon of assurance, offering a structured approach to integrating security measures seamlessly into the software development process. Let’s delve into the importance and myriad benefits of implementing SSDLC.
Understanding SSDLC:
The SSDLC methodology revolves around weaving security practices into each phase of the software development lifecycle. Unlike traditional models where security is often an afterthought, SSDLC embeds security considerations from the initial design phase through deployment and maintenance, ensuring a proactive stance against vulnerabilities and threats.
Importance of SSDLC Implementation:
- Early Identification of Vulnerabilities: By integrating security assessments and testing right from the outset, SSDLC facilitates the early detection and mitigation of potential vulnerabilities. Addressing security concerns at the nascent stages of development minimizes the risk of costly fixes and breaches down the line.
- Enhanced Risk Management: SSDLC enables organizations to adopt a risk-based approach to security, prioritizing the allocation of resources and efforts based on the severity and likelihood of potential threats. This proactive risk management strategy fosters a robust security posture while optimizing resource utilization.
- Compliance and Regulatory Alignment: In an era marked by stringent data protection regulations and compliance standards, SSDLC serves as a guiding framework for ensuring adherence to regulatory requirements. By integrating compliance checks and controls throughout the development process, organizations can navigate regulatory landscapes with confidence.
- Cultivating a Security-Centric Culture: Implementing SSDLC fosters a culture of security consciousness across the organization. By instilling security awareness and best practices among developers, testers, and stakeholders, organizations can cultivate a collective commitment to safeguarding digital assets and maintaining trust.
- Cost-Efficient Security Measures: While the initial investment in implementing SSDLC may seem significant, the long-term benefits far outweigh the costs. By preemptively addressing security vulnerabilities and minimizing the likelihood of breaches, organizations can mitigate the substantial financial and reputational damages associated with cyber incidents.
Benefits of SSDLC Implementation:
- Reduced Time to Market: Contrary to the misconception that stringent security measures impede innovation and agility, SSDLC streamlines the development process, leading to faster time-to-market. By integrating security testing seamlessly into development workflows, organizations can accelerate the delivery of secure, high-quality software products.
- Improved Software Quality: SSDLC emphasizes the importance of robust testing and validation procedures, resulting in software products that exhibit enhanced reliability, resilience, and functionality. By fostering a culture of quality assurance and continuous improvement, organizations can deliver superior user experiences while minimizing the occurrence of software defects and vulnerabilities.
- Heightened Customer Trust and Confidence: In an era marred by frequent data breaches and cyber threats, customers are increasingly discerning when it comes to entrusting their sensitive information to software products and services. By embracing SSDLC, organizations can bolster customer trust and confidence by demonstrating a steadfast commitment to security and privacy.
- Proactive Threat Mitigation: SSDLC empowers organizations to proactively identify, assess, and mitigate security threats throughout the software development lifecycle. By leveraging threat modeling, code reviews, and penetration testing, organizations can identify and remediate vulnerabilities before they can be exploited by malicious actors, thereby minimizing the risk of security incidents.
- Adaptability and Scalability: SSDLC is not a one-size-fits-all approach; rather, it is adaptable to the unique requirements and constraints of diverse organizations and projects. Whether developing web applications, mobile apps, or enterprise software solutions, SSDLC principles can be tailored and scaled to suit the specific needs of each endeavor.
Addressing the Challenges of Implementing SSDLC
In today’s fast-paced digital landscape, where cyber threats loom large and data breaches are an ever-present danger, the implementation of robust security measures has become paramount. Among these measures, the Secure Software Development Life Cycle (SSDLC) stands out as a crucial framework for ensuring that security is integrated into every phase of software development. However, despite its importance, implementing SSDLC can pose significant challenges for organizations. In this article, we delve into these challenges and explore strategies for addressing them effectively.
- Cultural Shift: One of the foremost challenges in implementing SSDLC is fostering a culture of security consciousness within the organization. This requires a paradigm shift where security is not viewed as an afterthought but rather as an integral part of the development process. Achieving this cultural transformation demands commitment from leadership, effective communication across teams, and continuous education and training initiatives to instill security best practices.
- Resource Constraints: Another hurdle organizations often face is resource constraints, both in terms of skilled personnel and budgetary limitations. Building and maintaining a competent security team capable of implementing SSDLC can be a daunting task. To overcome this challenge, organizations can leverage external expertise through partnerships with managed security service providers or invest in training programs to upskill existing personnel.
- Integration with DevOps: The integration of SSDLC with DevOps practices poses a unique set of challenges. While DevOps emphasizes rapid and continuous delivery, security measures such as thorough code reviews and vulnerability assessments may appear to slow down the development process. Balancing the need for speed with security requires careful planning, automation of security testing processes, and the adoption of tools that seamlessly integrate security into the DevOps pipeline.
- Complexity of Software Ecosystems: Modern software ecosystems are characterized by their complexity, with applications often relying on a multitude of third-party libraries, APIs, and dependencies. Managing the security implications of this interconnectedness can be overwhelming. Implementing robust measures such as comprehensive vulnerability management, strict access controls, and regular security audits is essential to mitigate risks associated with third-party components.
- Compliance and Regulatory Requirements: Compliance with industry regulations and data protection laws adds another layer of complexity to SSDLC implementation. Ensuring that security measures align with regulatory requirements such as GDPR, HIPAA, or PCI DSS demands meticulous planning and adherence to standards and frameworks. Organizations must stay abreast of evolving regulations and adjust their security practices accordingly to avoid non-compliance penalties.
- Legacy Systems and Legacy Mindsets: Legacy systems pose a significant challenge to SSDLC implementation, as they often lack built-in security features and are more susceptible to vulnerabilities. Additionally, entrenched legacy mindsets resistant to change can hinder efforts to implement modern security practices. Overcoming these challenges requires a phased approach, gradually modernizing legacy systems while simultaneously addressing cultural resistance through education and incentivization.
Cultural Shift: Fostering Security Mindset Across Teams
In today’s ever-evolving digital landscape, the significance of security within organizations cannot be overstated. With cyber threats becoming increasingly sophisticated, fostering a security mindset across teams has emerged as a critical necessity. This cultural shift isn’t just about implementing the latest security tools and protocols; it’s about ingraining a proactive approach to security in every aspect of operations. Let’s delve into how organizations can effectively foster a security-first culture across their teams.
Understanding the Importance
First and foremost, it’s essential to recognize why fostering a security mindset is paramount. Cyber threats loom large, with data breaches, ransomware attacks, and phishing scams making headlines regularly. The repercussions of such breaches extend beyond financial losses to tarnished reputations and compromised customer trust. By instilling a security-first culture, organizations can mitigate these risks and safeguard sensitive data, intellectual property, and customer information.
Leadership Commitment
Building a security-first culture starts at the top. Leadership commitment is crucial in setting the tone and prioritizing security across the organization. When leaders champion security initiatives, employees are more likely to perceive security as a priority rather than an afterthought. By allocating resources, providing necessary training, and integrating security into strategic decision-making, leaders can demonstrate their unwavering commitment to fostering a culture of security.
Education and Awareness
Education is the cornerstone of fostering a security mindset. Employees must be equipped with the knowledge and skills to recognize potential threats and respond appropriately. Regular training sessions, workshops, and simulations can empower employees to identify phishing attempts, safeguard sensitive information, and adhere to security best practices. Additionally, cultivating a culture of open communication encourages employees to report suspicious activities promptly, fostering a collective responsibility for security.
Integration into Workflows
Embedding security into everyday workflows is essential for its long-term sustainability. Rather than viewing security as a separate function, it should be seamlessly integrated into existing processes. This includes incorporating security checkpoints in project lifecycles, conducting regular security assessments, and ensuring compliance with industry regulations. By making security an inherent part of operations, organizations can minimize vulnerabilities and strengthen their overall security posture.
Collaboration and Accountability:
A security-first culture thrives on collaboration and accountability. Siloed approaches to security are ineffective in today’s interconnected landscape. Cross-functional collaboration encourages knowledge sharing, facilitates threat intelligence sharing, and enables swift incident response. Moreover, holding individuals and teams accountable for security lapses fosters a sense of ownership and reinforces the importance of adhering to security policies and procedures.
Continuous Improvement:
In the realm of cybersecurity, complacency is not an option. Threats evolve rapidly, necessitating continuous adaptation and improvement. Organizations must foster a culture of continuous learning and improvement, where feedback is embraced, and lessons learned from past incidents are used to bolster defenses. By staying abreast of emerging threats, leveraging the latest technologies, and refining existing security measures, organizations can stay one step ahead of cyber adversaries.
Resource Allocation: Balancing Security Needs with Project Timelines
In today’s rapidly evolving digital landscape, the importance of cybersecurity cannot be overstated. With cyber threats becoming increasingly sophisticated, organizations must prioritize security measures to safeguard sensitive data and maintain the trust of their stakeholders. However, achieving robust cybersecurity often requires significant time and resources, which can sometimes conflict with project timelines.
Resource allocation plays a crucial role in striking a balance between security needs and project deadlines. Here, we delve into strategies that organizations can employ to effectively manage this delicate equilibrium.
1. Risk Assessment and Prioritization: Before embarking on any project, it’s essential to conduct a thorough risk assessment to identify potential security vulnerabilities. This involves evaluating the likelihood and impact of various threats and vulnerabilities. By understanding the specific risks associated with a project, organizations can prioritize security measures based on their potential impact on the business.
2. Adopt a Proactive Security Approach: Rather than treating security as an afterthought, organizations should integrate it into every stage of the project lifecycle. This includes implementing security protocols during the planning, development, implementation, and maintenance phases. By adopting a proactive approach to security, organizations can mitigate risks early on, minimizing the need for costly fixes and delays down the line.
3. Invest in Automation and Integration: Automation can streamline security processes, enabling organizations to achieve greater efficiency without compromising on security standards. By leveraging automated tools for tasks such as threat detection, vulnerability scanning, and patch management, organizations can reduce the time and effort required to maintain a secure environment. Additionally, integrating security measures into existing systems and workflows can help minimize disruption to project timelines.
4. Agile Development Practices: Agile methodologies promote flexibility and adaptability, allowing organizations to respond quickly to changing security requirements without derailing project timelines. By breaking down projects into smaller, manageable iterations, teams can address security concerns incrementally, making it easier to maintain the balance between security and efficiency.
5. Allocate Adequate Resources: While it’s essential to optimize resource allocation, cutting corners on security can have severe consequences in the long run. Organizations must allocate sufficient resources, including budget, personnel, and technology, to support robust security measures. By investing in the right tools and expertise, organizations can enhance their security posture without unduly burdening project timelines.
6. Continuous Monitoring and Improvement: Security is not a one-time endeavor but an ongoing process that requires constant vigilance. By implementing continuous monitoring and improvement practices, organizations can identify and address security gaps in real-time, minimizing the risk of breaches or disruptions. This iterative approach enables organizations to adapt to evolving threats while maintaining project momentum.
Integration with Agile and DevOps Methodologies
In today’s fast-paced digital landscape, businesses are constantly seeking ways to enhance their efficiency and productivity. Two methodologies that have gained significant traction in recent years are Agile and DevOps. While both are highly effective on their own, integrating them can lead to even greater success and streamlined operations.
Agile methodology, rooted in iterative development and collaboration, focuses on delivering high-quality software in short, incremental cycles. It promotes adaptability to change and customer-centricity, enabling teams to respond quickly to shifting requirements and market demands. On the other hand, DevOps emphasizes collaboration and automation across development and operations teams to accelerate the delivery of software while maintaining reliability and stability.
The integration of Agile and DevOps methodologies brings together the best of both worlds, fostering a culture of continuous improvement and innovation. By aligning development, operations, and quality assurance functions, organizations can break down silos and promote seamless communication and collaboration among teams. This alignment ensures that the entire software delivery pipeline operates smoothly, from ideation to deployment and beyond.
One of the key benefits of integrating Agile and DevOps is the accelerated delivery of value to customers. Agile’s iterative approach allows for frequent releases of usable software increments, while DevOps automates the deployment and monitoring processes, enabling faster delivery without sacrificing quality. This increased speed-to-market not only enhances customer satisfaction but also provides organizations with a competitive edge in today’s rapidly evolving market landscape.
Moreover, the integration of Agile and DevOps promotes a culture of continuous feedback and improvement. Agile’s emphasis on retrospectives encourages teams to reflect on their processes and identify areas for enhancement, while DevOps’ automation capabilities facilitate rapid iteration and experimentation. By continuously evaluating and refining their practices, organizations can adapt to changing requirements and market dynamics more effectively.
Furthermore, the integration of Agile and DevOps enables organizations to achieve greater operational efficiency and cost savings. By automating repetitive tasks and streamlining workflows, teams can reduce manual errors and overhead, resulting in lower operational costs and faster time-to-market. Additionally, the increased collaboration and transparency fostered by this integration minimize rework and delays, further optimizing resource utilization and maximizing ROI.
Regulatory Compliance and Legal Considerations
In the ever-evolving landscape of business, regulatory compliance and legal considerations stand as crucial pillars for any organization’s success and sustainability. Whether you’re a startup or a multinational corporation, understanding and adhering to regulatory requirements and legal obligations is paramount. Failure to comply can lead to hefty fines, legal entanglements, and irreparable damage to your reputation. In this guide, we’ll delve into the intricacies of regulatory compliance and legal considerations, providing insights to help you navigate this complex terrain.
Understanding Regulatory Compliance:
Regulatory compliance refers to the process of ensuring that an organization abides by laws, regulations, guidelines, and specifications relevant to its operations. These regulations can span various domains, including finance, healthcare, data privacy, environmental protection, and more. Compliance requirements are often set forth by governmental bodies, industry regulators, or international standards organizations.
To establish an effective compliance program, organizations must first identify the relevant regulations applicable to their industry and geographic locations. This entails conducting thorough research and engaging with legal experts or consultants specializing in regulatory compliance. Once identified, policies and procedures should be developed to ensure ongoing adherence to these regulations. Regular audits and assessments are essential to evaluate compliance levels and identify areas for improvement.
Key Legal Considerations:
Legal considerations encompass a broad spectrum of issues that businesses must address to operate ethically and within the confines of the law. These considerations include but are not limited to:
- Corporate Governance: Ensuring that the organization’s decision-making processes align with legal requirements and ethical standards.
- Intellectual Property Protection: Safeguarding intellectual property rights through patents, trademarks, copyrights, and trade secrets.
- Contracts and Agreements: Drafting, negotiating, and executing contracts with stakeholders, suppliers, customers, and employees to mitigate legal risks and ensure enforceability.
- Employment Law: Complying with labor laws, including employment contracts, wage and hour regulations, workplace safety, discrimination, and harassment policies.
- Data Privacy and Security: Adhering to data protection laws and implementing robust cybersecurity measures to safeguard sensitive information.
- Antitrust and Competition Law: Avoiding anticompetitive behavior and ensuring compliance with regulations aimed at promoting fair competition in the marketplace.
Best Practices for Compliance and Legal Risk Management:
- Establish a Compliance Culture: Foster a culture of compliance from the top down, emphasizing the importance of ethical conduct and regulatory adherence throughout the organization.
- Invest in Education and Training: Provide comprehensive training programs to educate employees about relevant regulations, legal obligations, and ethical standards.
- Implement Compliance Technologies: Leverage technology solutions such as compliance management software to streamline processes, automate compliance tasks, and facilitate regulatory reporting.
- Conduct Regular Audits and Risk Assessments: Perform periodic audits and risk assessments to evaluate compliance levels, identify potential risks, and implement corrective measures proactively.
- Stay Informed and Adapt: Keep abreast of regulatory developments, legislative changes, and emerging legal trends that may impact your business operations, and adjust your compliance strategies accordingly.
Future Trends and Innovations in SSDLC
In the rapidly evolving landscape of cybersecurity, staying ahead of the curve is not just an advantage but a necessity. One crucial aspect of this realm is the Secure Software Development Life Cycle (SSDLC), a methodology ensuring that security is integrated into every phase of software development. As technology advances and threats become more sophisticated, the future of SSDLC promises to be both transformative and indispensable. Let’s delve into the anticipated trends and innovations that will shape the SSDLC landscape in the coming years.
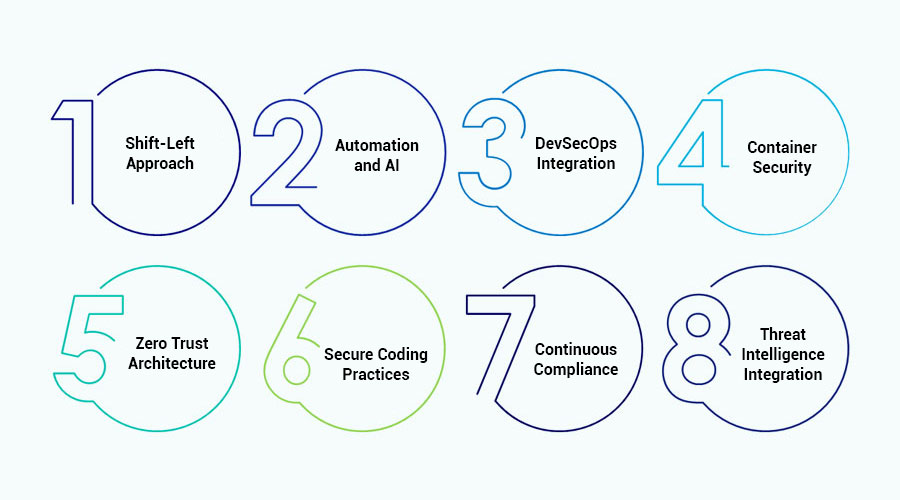
- Shift-Left Approach: The traditional SSDLC model emphasizes security towards the end of the development cycle. However, the future lies in adopting a “shift-left” approach, integrating security from the initial stages of development. By identifying and mitigating vulnerabilities early on, organizations can minimize risks and reduce the cost of remediation.
- Automation and AI: As the volume and complexity of software projects continue to increase, manual security testing processes become impractical. Automation, coupled with Artificial Intelligence (AI) and Machine Learning (ML), will play a pivotal role in enhancing the efficiency and effectiveness of SSDLC. Automated tools can identify security flaws, analyze code patterns, and provide real-time insights, enabling developers to build more secure software rapidly.
- DevSecOps Integration: The integration of security into DevOps practices, known as DevSecOps, is gaining traction as organizations strive for seamless collaboration between development, operations, and security teams. In the future, DevSecOps will become the standard approach, fostering a culture of shared responsibility and accountability for security throughout the software development lifecycle.
- Container Security: With the widespread adoption of containerization technologies like Docker and Kubernetes, ensuring the security of containerized applications becomes paramount. Future SSDLC frameworks will include specialized measures for container security, such as vulnerability scanning, image signing, and runtime protection, to mitigate risks associated with containerized environments.
- Zero Trust Architecture: In an era of increasing cyber threats, the traditional perimeter-based security model is no longer sufficient. Zero Trust Architecture (ZTA) adopts a “never trust, always verify” approach, requiring strict authentication and authorization for every access attempt. Future SSDLC methodologies will embrace ZTA principles, implementing robust identity and access management controls to safeguard software assets against unauthorized access and insider threats.
- Secure Coding Practices: As the foundation of software security, adopting secure coding practices is imperative for minimizing vulnerabilities and ensuring the resilience of applications. Future SSDLC frameworks will emphasize the importance of training developers in secure coding techniques, conducting code reviews, and leveraging static and dynamic analysis tools to identify and remediate security flaws early in the development process.
- Continuous Compliance: With the proliferation of data protection regulations such as GDPR, CCPA, and HIPAA, compliance with regulatory requirements is a top priority for organizations worldwide. Future SSDLC methodologies will incorporate mechanisms for continuous compliance monitoring, enabling automated assessment of software against regulatory standards and facilitating timely remediation of compliance issues.
- Threat Intelligence Integration: Understanding emerging threats and attack vectors is essential for building robust security defenses. Future SSDLC frameworks will integrate threat intelligence feeds, leveraging advanced analytics and threat modeling techniques to anticipate and mitigate potential security risks proactively.
Top Secure Software Development Companies
In an era where digital security is paramount, the demand for secure software development companies has never been higher. With cyber threats evolving at an alarming rate, businesses across industries are seeking reliable partners to fortify their digital infrastructure. In this article, we’ll explore the top five secure software development companies that are at the forefront of safeguarding data and mitigating risks in today’s digital landscape.
-
-
Next Big Technology:

Focus Area
- Mobile App Development
- App Designing (UI/UX)
- Software Development
- Web Development
- AR & VR Development
- Big Data & BI
- Cloud Computing Services
- DevOps
- E-commerce Development
Industries Focus
- Art, Entertainment & Music
- Business Services
- Consumer Products
- Designing
- Education
- Financial & Payments
- Gaming
- Government
- Healthcare & Medical
- Hospitality
- Information Technology
- Legal & Compliance
- Manufacturing
- Media
-
- Checkmarx: Renowned for its cutting-edge Static Application Security Testing (SAST) and Software Composition Analysis (SCA) solutions, Checkmarx empowers organizations to build secure software without compromising on speed or innovation. Their platform offers deep code analysis, helping developers identify and remediate vulnerabilities early in the development process.
- Veracode: As a pioneer in cloud-based application security testing, Veracode enables businesses to scale their security programs efficiently. Their dynamic and static analysis tools provide actionable insights to developers, enabling them to write secure code from the outset. Veracode’s emphasis on automation and integration simplifies the security process without sacrificing accuracy.
- Rapid7: Specializing in vulnerability management and threat detection, Rapid7 equips organizations with the tools needed to proactively identify and address security risks. Their solutions span across application security, network security, and cloud security, offering a holistic approach to safeguarding digital assets. Rapid7’s intuitive interfaces and actionable reports empower businesses to make informed security decisions.
- Fortinet: Recognized for its robust cybersecurity platform, Fortinet delivers end-to-end protection against today’s most advanced threats. With a focus on both network and application security, Fortinet’s solutions seamlessly integrate into existing infrastructure, providing real-time threat intelligence and proactive defense mechanisms. Their commitment to innovation ensures that businesses stay ahead of evolving cyber threats.
FAQs On Secure Software Development
In the fast-paced digital landscape, secure software development is paramount for safeguarding sensitive data, maintaining user trust, and ensuring business continuity. However, navigating the intricacies of secure software development can be daunting for many. To shed light on this vital aspect of software engineering, let’s delve into some frequently asked questions (FAQs) surrounding secure software development.
1. What is Secure Software Development?
Secure software development refers to the process of designing, building, and deploying software applications with robust security features and measures integrated from the outset. It involves identifying potential security risks, implementing appropriate safeguards, and adhering to best practices to mitigate vulnerabilities and protect against cyber threats.
2. Why is Secure Software Development Important?
The importance of secure software development cannot be overstated. In today’s digital ecosystem, where cyber threats are prevalent, a single security breach can have devastating consequences, ranging from financial losses to reputational damage. Secure software development not only helps in safeguarding sensitive data but also fosters trust among users, enhances brand reputation, and ensures regulatory compliance.
3. What are the Key Principles of Secure Software Development?
Several key principles underpin secure software development:
- Principle of Least Privilege: Granting users and processes only the minimum level of access required to perform their tasks.
- Defense in Depth: Implementing multiple layers of security controls to mitigate risks at various levels.
- Secure by Design: Integrating security considerations into every phase of the software development lifecycle.
- Continuous Monitoring: Regularly assessing and monitoring systems for potential security threats and vulnerabilities.
- Regular Updates and Patch Management: Ensuring that software components are up-to-date with the latest security patches and fixes.
4. What Are the Common Security Vulnerabilities in Software Development?
Common security vulnerabilities include:
- Injection Attacks: Such as SQL injection, where malicious code is injected into input fields to manipulate databases.
- Cross-Site Scripting (XSS): Where attackers inject malicious scripts into web pages viewed by other users.
- Insecure Authentication and Authorization: Weak authentication mechanisms or inadequate authorization checks can lead to unauthorized access.
- Insecure Direct Object References: Allowing attackers to manipulate object references to access unauthorized data.
- Security Misconfigurations: Improperly configured security settings that leave systems vulnerable to exploitation.
5. How Can Developers Ensure Secure Coding Practices?
Developers can adopt the following practices to ensure secure coding:
- Input Validation: Validate and sanitize all user inputs to prevent injection attacks.
- Use of Secure Libraries and Frameworks: Utilize well-established libraries and frameworks with built-in security features.
- Encryption: Encrypt sensitive data both at rest and in transit using strong encryption algorithms.
- Secure Coding Standards: Adhere to established coding standards, such as OWASP’s Secure Coding Practices or CERT Secure Coding Standards.
- Code Reviews and Testing: Conduct regular code reviews and thorough security testing, including static and dynamic analysis, to identify and rectify vulnerabilities.
6. How Can Organizations Promote a Culture of Secure Software Development?
Organizations can foster a culture of secure software development by:
- Training and Awareness Programs: Providing comprehensive training and awareness programs to educate developers and stakeholders about security best practices.
- Establishing Security Policies: Implementing clear security policies and guidelines that govern the entire software development lifecycle.
- Integration of Security into DevOps: Embedding security practices seamlessly into DevOps processes to promote collaboration between development and security teams.
- Incident Response Planning: Developing robust incident response plans to effectively mitigate and manage security incidents when they occur.
- Regular Audits and Compliance Checks: Conducting regular security audits and compliance checks to ensure adherence to industry standards and regulatory requirements.
Thanks for reading our post “Secure Software Development Life Cycle – Benefits Stages and Challenges”. Please connect with us to learn more about Best Secure Software Development Life Cycle.