Table of Contents
Understanding Client-Server Architecture
In the realm of computer networking and distributed systems, the client-server architecture stands as a cornerstone, facilitating communication between devices and enabling the seamless exchange of information across networks. Understanding its intricacies is crucial for anyone delving into the world of modern computing. In this article, we’ll embark on a journey to unravel the mysteries of client-server architecture, exploring its fundamentals, components, and real-world applications.
Breaking Down Client-Server Architecture
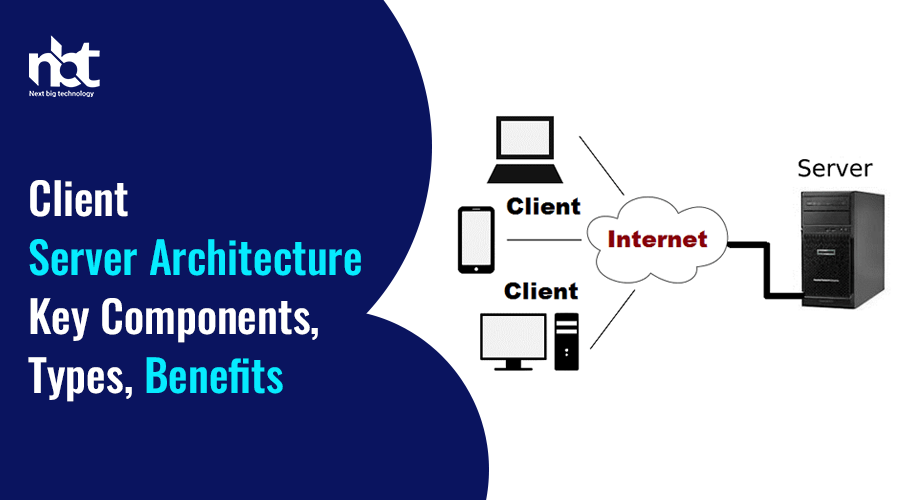
At its core, client-server architecture embodies a model where computational tasks and resources are divided between clients and servers, each fulfilling distinct roles within a networked environment. The interaction typically follows a request-response paradigm, where clients initiate requests for services or resources, and servers respond by providing the requested data or performing the requested task.
Key Components:
- Client: The client refers to any device or application that initiates communication by sending requests to servers. It could be a computer, smartphone, or any other network-enabled device running client software.
- Server: On the flip side, servers are dedicated computers or software applications designed to respond to client requests. They store and manage resources, such as files, databases, or services, and serve them upon request.
- Network: The network serves as the medium through which clients and servers communicate. It can be a local area network (LAN), wide area network (WAN), or the internet itself.
How It Works:
When a client seeks a service or resource, it sends a request over the network to the appropriate server. The server, equipped with specialized software, processes the request, retrieves the necessary data or performs the requested operation, and sends the result back to the client. This exchange follows a standardized protocol, ensuring seamless communication between heterogeneous systems.
Real-World Applications:
1. Web Browsing: Every time you access a website, your browser acts as the client, sending requests to web servers hosting the desired content. The server, in turn, responds by transmitting web pages, images, or other resources, enabling you to browse the internet effortlessly.
2. Email: Email operates on a client-server model, where email clients such as Outlook or Gmail communicate with mail servers to send and receive messages. The servers store and manage the emails, ensuring reliable delivery across the network.
3. Online Gaming: In multiplayer online games, clients connect to dedicated game servers to participate in virtual worlds and engage with other players. These servers coordinate game sessions, handle player interactions, and synchronize game states to provide a seamless gaming experience.
Benefits of Client-Server Architecture:
- Scalability: By distributing tasks between clients and servers, the architecture scales efficiently to accommodate growing user demands and resource requirements.
- Centralized Management: Servers centralize data and resources, allowing for easier management, security enforcement, and maintenance.
- Resource Sharing: Clients can access shared resources hosted on servers, fostering collaboration and efficient utilization of computing resources.
Key Components of Client-Server Systems
In the realm of modern computing, client-server systems stand as the backbone of countless applications and services, facilitating seamless communication and interaction between users and servers. Understanding the key components of these systems is essential for developers, engineers, and anyone involved in the world of technology. In this article, we delve into the fundamental elements that constitute client-server systems, shedding light on their roles and significance.
- Clients: At the forefront of any client-server architecture are the clients. These are the end-user devices or applications that initiate requests to the server. Clients can range from web browsers, mobile apps, desktop applications, to IoT devices. Their primary function is to send requests to the server for specific resources or services, such as accessing a webpage, retrieving data from a database, or uploading a file.
- Servers: Opposite to clients are servers, the central component of the client-server model. Servers are powerful computers or software applications responsible for responding to client requests by providing the requested resources or performing the necessary computations. Servers can vary in their functions, including web servers, database servers, email servers, and file servers. Each server specializes in handling specific types of requests and executing corresponding actions.
- Protocols: Facilitating communication between clients and servers are protocols, which define the rules and conventions for data exchange. One of the most common protocols used in client-server systems is the Hypertext Transfer Protocol (HTTP), widely employed for web communication. Other notable protocols include FTP (File Transfer Protocol), SMTP (Simple Mail Transfer Protocol), and TCP/IP (Transmission Control Protocol/Internet Protocol). These protocols ensure that data transmission between clients and servers is secure, reliable, and standardized.
- Middleware: Serving as the intermediary between clients and servers, middleware plays a crucial role in client-server systems. Middleware comprises software components and services that facilitate communication, data management, and application integration between diverse computing systems. It abstracts the complexities of communication protocols and enables interoperability between different platforms and technologies. Examples of middleware include message brokers, application servers, and remote procedure call (RPC) mechanisms.
- Database Management Systems (DBMS): In many client-server applications, data storage and retrieval are vital functionalities handled by Database Management Systems. DBMSs provide a structured and organized way to store, manage, and manipulate data. They allow multiple clients to access and modify data concurrently while ensuring data integrity and security. Popular examples of DBMSs include MySQL, Oracle, PostgreSQL, and MongoDB.
- Security Mechanisms: Security is paramount in client-server systems to protect sensitive data and ensure the integrity and confidentiality of communications. Various security mechanisms are employed to safeguard client-server interactions, including encryption, authentication, authorization, and data validation. Secure Socket Layer (SSL) and Transport Layer Security (TLS) protocols are commonly used to encrypt data transmitted between clients and servers, preventing unauthorized access and eavesdropping.
- Load Balancers: In high-traffic client-server environments, load balancers play a critical role in distributing incoming client requests across multiple servers to optimize performance and ensure scalability. Load balancers monitor server health, allocate resources efficiently, and prevent any single server from becoming overwhelmed with requests. By evenly distributing the workload, load balancers enhance the responsiveness and reliability of client-server applications.
Types of Client-Server Architectures
In the realm of computer networking, client-server architectures serve as the backbone for a multitude of applications, facilitating communication and data exchange between clients and servers. These architectures come in various forms, each with its unique characteristics and suitability for different scenarios. Let’s delve into the types of client-server architectures that power the digital landscape:
- Two-Tier Architecture: This is the most basic form of client-server architecture, consisting of a client application directly communicating with a server. Typically, the client handles the presentation layer, while the server manages the data storage and business logic. Two-tier architectures are straightforward to implement but can suffer from scalability and maintenance issues as the application grows.
- Three-Tier Architecture: Three-tier architecture introduces an additional layer between the client and server, known as the application or middleware layer. This layer acts as an intermediary, separating the presentation logic from the business logic and database management. Three-tier architectures offer improved scalability, modularity, and flexibility compared to two-tier systems.
- Multi-Tier Architecture: Multi-tier architecture expands upon the three-tier model by incorporating multiple layers of servers to distribute the workload and enhance performance. Common tiers include presentation, application, business logic, and data storage layers. This architecture is highly scalable and fault-tolerant, making it suitable for large-scale enterprise applications and distributed systems.
- Peer-to-Peer (P2P) Architecture: In contrast to traditional client-server models, peer-to-peer architecture enables direct communication between individual nodes or peers without the need for central servers. Peers act both as clients and servers, sharing resources and services among themselves. P2P architectures excel in decentralized environments and are commonly used in file-sharing networks and distributed computing systems.
- Proxy Server Architecture: Proxy server architecture employs intermediary servers, known as proxies, to handle client requests and forward them to the appropriate destination servers. Proxies can cache frequently accessed content, filter incoming requests, and enhance security by acting as a barrier between clients and servers. This architecture is commonly used to improve performance, security, and network efficiency.
- Microservices Architecture: Microservices architecture decomposes applications into small, independently deployable services, each serving a specific function or feature. Clients interact with these services through APIs, enabling greater agility, scalability, and resilience. Microservices promote modular development, allowing teams to work on different components concurrently and deploy updates without disrupting the entire system.
- Serverless Architecture: Serverless architecture abstracts away the underlying infrastructure, allowing developers to focus solely on writing code. Functions are triggered by events and executed in ephemeral containers, eliminating the need for provisioning and managing servers. Serverless architectures offer automatic scaling, cost-efficiency, and rapid development cycles, making them ideal for event-driven and highly scalable applications.
Client-Side Components in Client-Server Architecture
In the realm of modern technology, the client-server architecture stands as a cornerstone, facilitating communication and data exchange between clients and servers. At the heart of this architecture lies the interaction between client-side and server-side components. In this article, we delve into the significance of client-side components in the client-server model, elucidating their role and importance in shaping user experiences and system functionalities.
Client-side components, also known as front-end components, encompass the software and interfaces that operate directly on the user’s device, such as web browsers or mobile applications. Unlike server-side components, which handle data processing and storage on remote servers, client-side components primarily focus on presenting information to users and facilitating interactions.
One of the primary functions of client-side components is to render user interfaces and provide an intuitive and interactive platform for users to engage with. Through technologies like HTML, CSS, and JavaScript, developers craft visually appealing and responsive interfaces that enhance user experience. These components enable users to interact with web pages, submit forms, navigate menus, and perform various actions seamlessly.
Moreover, client-side components play a pivotal role in optimizing performance and reducing server load. By offloading certain tasks to the client side, such as form validation, data processing, and caching, server resources are conserved, leading to faster response times and improved scalability. This distributed approach to computing not only enhances system efficiency but also ensures a smoother and more responsive user experience, especially in scenarios with high user traffic.
Another crucial aspect of client-side components is their ability to enable dynamic content generation and personalized experiences. Through techniques like AJAX (Asynchronous JavaScript and XML) and Single Page Applications (SPAs), web applications can retrieve and display data without requiring full page reloads, resulting in a fluid and dynamic browsing experience. Additionally, client-side scripting languages empower developers to tailor content based on user preferences, behavior, and contextual information, thereby enhancing engagement and satisfaction.
Furthermore, client-side components contribute to the security of client-server applications by implementing measures such as input validation, encryption, and authentication directly on the user’s device. By validating user inputs and encrypting sensitive data before transmission, the risk of security breaches and data manipulation is mitigated, bolstering the overall integrity and trustworthiness of the system.
Request-Response Paradigm in Client-Server Systems
In the digital realm where communication between devices is paramount, the request-response paradigm stands as a fundamental concept in client-server systems. This paradigm governs the interaction between a client, which initiates requests, and a server, which responds to those requests. Understanding this paradigm is crucial for developers, network engineers, and anyone involved in designing or maintaining distributed systems. Let’s delve into the intricacies of this foundational concept.
What is the Request-Response Paradigm?
At its core, the request-response paradigm is a communication pattern wherein a client sends a request to a server, and the server responds to that request. This exchange forms the backbone of interactions in various networked environments, including web browsing, email services, and database management.
How Does it Work?
- Client Sends a Request: The process commences when a client, typically a device or application, initiates a request to a server. This request contains specific instructions or queries, such as fetching a web page, retrieving data, or performing an action.
- Server Processes the Request: Upon receiving the request, the server interprets the instructions or queries embedded within it. This may involve accessing databases, executing scripts, or performing other tasks necessary to fulfill the request.
- Server Generates a Response: Once the server processes the request, it generates a response containing the requested data or indicating the outcome of the action. This response is then sent back to the client.
- Client Receives and Processes the Response: Finally, the client receives the response from the server and processes it accordingly. This may involve rendering a web page, displaying retrieved data, or executing further actions based on the response received.
Key Components
- Request: This is the initial communication sent by the client to the server. It typically contains specific headers, parameters, and sometimes a payload, depending on the nature of the request.
- Response: The server’s reply to the client’s request. It includes status information (such as success or failure), headers providing metadata about the response, and often a payload containing the requested data or an indication of the outcome.
Benefits of the Request-Response Paradigm
- Modularity and Scalability: By decoupling the client and server, this paradigm enables modular development and scalability. Clients can be developed independently of servers, and vice versa, allowing for easier maintenance and upgrades.
- Standardization: The request-response paradigm follows established protocols and standards, such as HTTP in web-based systems. This ensures interoperability between different client and server implementations.
- Efficiency: The asynchronous nature of request-response communication allows clients to continue other tasks while awaiting a response from the server. This enhances overall system efficiency and responsiveness.
Challenges and Considerations
- Latency: Depending on network conditions and server load, there may be delays in receiving responses, leading to latency issues.
- Security: Transmitting sensitive data between client and server requires robust security measures to prevent interception or unauthorized access.
- Error Handling: Effective error handling mechanisms are crucial to address failures in communication, ensuring reliable operation of the system.
Distributed Client-Server Architecture
In the realm of modern computing, distributed client-server architecture stands tall as a cornerstone of efficient and scalable systems. This architectural paradigm revolutionizes the way applications function by distributing tasks and responsibilities across multiple interconnected nodes. Let’s delve into the depths of this architecture to understand its workings, advantages, and applications.
Understanding Distributed Client-Server Architecture:
At its core, distributed client-server architecture embodies the principle of decentralization. Unlike traditional client-server models where a single server handles all requests from clients, in a distributed setup, the workload is distributed among multiple servers. Each server, known as a node, operates independently yet collaboratively to fulfill client requests.
Key Components and Workings:
-
-
- Clients: These are the end-user devices that initiate requests to the servers. Clients can range from personal computers and smartphones to IoT devices.
- Servers: In a distributed setup, multiple servers work together to provide services to clients. Each server typically specializes in handling specific types of requests or tasks.
- Communication Infrastructure: Robust communication channels, such as the internet or a private network, facilitate seamless interaction between clients and servers.
- Load Balancer: To ensure even distribution of requests among servers, a load balancer intelligently routes incoming requests to the least busy server.
-
Advantages of Distributed Client-Server Architecture:
-
-
- Scalability: One of the most significant advantages is scalability. As the demand for services grows, additional servers can be easily added to the network, ensuring smooth performance without compromising on speed or reliability.
- Fault Tolerance: Distributed architectures enhance fault tolerance by distributing data and tasks across multiple nodes. In the event of a server failure, other nodes can seamlessly take over, preventing service disruptions.
- Performance Optimization: By distributing tasks across multiple servers, distributed architectures optimize performance and reduce latency. Clients can access services from the nearest server, minimizing network congestion and enhancing user experience.
- Resource Utilization: Distributed architectures maximize resource utilization by distributing workloads across multiple servers. This leads to efficient use of computing resources and reduces the risk of overloading any single server.
-
Applications of Distributed Client-Server Architecture:
-
- Cloud Computing: Leading cloud service providers leverage distributed architectures to offer scalable and resilient cloud computing services to businesses and individuals worldwide.
- Content Delivery Networks (CDNs): CDNs distribute content across geographically dispersed servers to deliver web content faster to users, irrespective of their location.
- Online Gaming: Multiplayer online games rely on distributed architectures to support large numbers of concurrent players while ensuring low latency and high performance.
- E-commerce Platforms: E-commerce platforms utilize distributed architectures to handle the influx of traffic during peak shopping seasons and ensure uninterrupted service delivery.
Scalability in Client-Server Architectures
In today’s digital landscape, scalability stands as the cornerstone of success for any application or system, particularly within client-server architectures. As businesses strive to meet growing demands and handle increasing user loads, the ability to scale efficiently becomes paramount. In this article, we delve into the concept of scalability within client-server architectures, exploring its significance, challenges, and strategies for achieving it seamlessly.
Understanding Scalability in Client-Server Architectures
At its core, scalability refers to the system’s capability to handle a growing amount of work, or its potential to be enlarged to accommodate that growth. In the context of client-server architectures, scalability encompasses both vertical and horizontal scaling:
- Vertical Scalability: Also known as scaling up, involves enhancing the existing server’s capabilities by adding more resources such as CPU, RAM, or storage. While vertical scaling offers simplicity in implementation, it has limitations regarding the maximum capacity a single server can handle.
- Horizontal Scalability: Also termed scaling out, entails distributing the workload across multiple servers or nodes. This approach allows for handling increased traffic by adding more servers to the architecture, thus providing better scalability and fault tolerance.
Challenges in Achieving Scalability
While scalability is essential for ensuring optimal performance and user experience, several challenges hinder its implementation:
- State Management: Managing the state across distributed servers poses a significant challenge, especially in horizontal scaling scenarios where sessions need to be maintained consistently.
- Data Consistency: Maintaining data consistency becomes complex in distributed environments, leading to challenges such as ensuring ACID properties in database transactions.
- Communication Overhead: Increased communication between servers can introduce latency and overhead, impacting performance negatively.
Strategies for Seamless Scalability
To address the challenges and achieve seamless scalability in client-server architectures, several strategies can be adopted:
- Decoupling Components: Breaking down the system into smaller, independent components allows for easier management and scaling of individual parts without affecting the entire architecture.
- Load Balancing: Implementing load balancers distributes incoming traffic evenly across multiple servers, ensuring optimal resource utilization and preventing overload on any single server.
- Caching: Utilizing caching mechanisms reduces the load on servers by storing frequently accessed data closer to the client, thus improving response times and scalability.
- Database Sharding: Partitioning databases into smaller, manageable shards distributed across multiple servers enhances scalability by distributing the database workload.
- Asynchronous Processing: Leveraging asynchronous communication and processing techniques minimizes blocking operations, allowing servers to handle a larger number of concurrent requests efficiently.
Load Balancing Techniques for Client-Server Systems
In today’s digital landscape, where the demand for online services continues to soar, ensuring seamless performance and optimal resource utilization in client-server systems is paramount. Load balancing techniques play a crucial role in distributing incoming traffic across multiple servers efficiently, thereby preventing overload and ensuring high availability. In this article, we delve into the intricacies of load balancing and explore some effective techniques employed in client-server architectures.
- Round Robin Load Balancing: Round Robin is one of the simplest load balancing algorithms wherein incoming requests are distributed across servers in a cyclic manner. Each server gets an equal share of requests, ensuring a balanced workload distribution. This technique is easy to implement and does not require sophisticated algorithms, making it ideal for basic setups.
- Least Connection Load Balancing: Unlike Round Robin, the Least Connection algorithm directs incoming requests to the server with the fewest active connections at any given time. By dynamically adjusting the load based on current connections, this technique ensures that servers with lighter loads handle more requests, thus optimizing resource utilization and minimizing response times.
- Weighted Round Robin: Weighted Round Robin extends the basic Round Robin approach by assigning weights to servers based on their processing capacity or hardware capabilities. Servers with higher weights receive a proportionally larger share of incoming requests, allowing administrators to fine-tune the load distribution according to each server’s capacity. This technique is particularly useful in heterogeneous server environments.
- IP Hash Load Balancing: IP Hash load balancing relies on hashing the client’s IP address to determine which server should handle the request. By consistently mapping the same client IP to the same server, this technique ensures session persistence, which is vital for applications requiring stateful connections, such as e-commerce platforms or online gaming.
- Dynamic Load Balancing: Dynamic load balancing techniques utilize real-time metrics, such as server health, response times, and current load, to intelligently route incoming requests. Algorithms like Least Response Time or Weighted Least Connections continuously monitor server performance and adjust traffic distribution accordingly. This adaptability enhances system scalability and resilience to sudden spikes in traffic.
- Content-Based Load Balancing: Content-based load balancing involves inspecting the content or type of incoming requests and directing them to servers optimized for handling specific types of content or processing tasks. This technique is beneficial for applications with diverse workload characteristics, such as multimedia streaming platforms or content delivery networks (CDNs).
- DNS Load Balancing: DNS load balancing leverages DNS servers to distribute incoming requests across multiple backend servers. By configuring DNS records with multiple IP addresses corresponding to different servers, incoming traffic is spread across the server pool. While simple to implement, DNS load balancing lacks granular control over traffic distribution and may suffer from DNS caching issues.
Security Considerations in Client-Server Architectures
In today’s interconnected digital world, client-server architectures serve as the backbone for numerous applications, ranging from email services to online banking platforms. However, as the volume and sensitivity of data exchanged between clients and servers continue to grow, ensuring robust security measures becomes paramount. In this article, we delve into the crucial security considerations that developers and system administrators must address to protect against potential threats in client-server architectures.
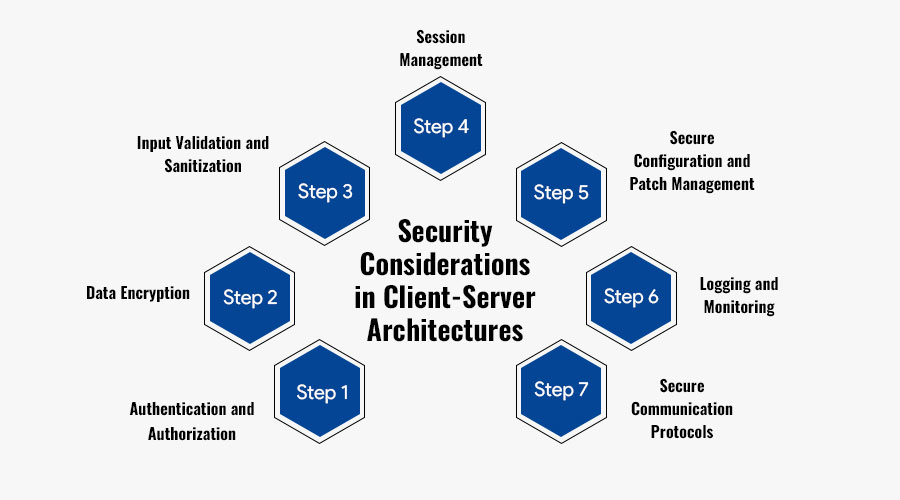
1. Authentication and Authorization: Authentication mechanisms are the first line of defense in any client-server interaction. It’s imperative to implement robust authentication protocols to verify the identities of both clients and servers. Techniques such as password authentication, biometric authentication, and multi-factor authentication (MFA) can bolster security by requiring users to provide multiple forms of verification. Furthermore, effective authorization mechanisms should be in place to control access to sensitive resources based on user roles and privileges.
2. Data Encryption: Encrypting data in transit and at rest is essential to prevent unauthorized access and eavesdropping. Transport Layer Security (TLS) protocols such as HTTPS encrypt communication channels between clients and servers, ensuring confidentiality and integrity. Additionally, employing strong encryption algorithms like AES (Advanced Encryption Standard) for storing sensitive data on servers adds an extra layer of protection against data breaches.
3. Input Validation and Sanitization: Client-server applications are vulnerable to various forms of attacks, including SQL injection, cross-site scripting (XSS), and buffer overflows. Implementing robust input validation and sanitization mechanisms can mitigate these risks by filtering and validating user inputs before processing them on the server. Utilizing parameterized queries for database interactions and input validation libraries can significantly reduce the likelihood of exploitation.
4. Session Management: Effective session management is critical to prevent session hijacking and unauthorized access to user accounts. Generating unique session identifiers, enforcing session timeouts, and securely storing session tokens can help thwart malicious attempts to compromise user sessions. Additionally, implementing secure cookie attributes such as HttpOnly and Secure can enhance the security of session cookies transmitted between clients and servers.
5. Secure Configuration and Patch Management: Maintaining secure configurations for both client and server components is essential to reduce the attack surface and minimize vulnerabilities. Regularly updating software components and applying security patches helps address known vulnerabilities and mitigate the risk of exploitation. Furthermore, adhering to security best practices such as disabling unnecessary services, configuring firewalls, and implementing intrusion detection systems (IDS) can enhance the overall security posture of client-server architectures.
6. Logging and Monitoring: Comprehensive logging and monitoring mechanisms play a crucial role in detecting and responding to security incidents effectively. By logging relevant events and activities across client and server components, administrators can gain insights into potential security breaches and anomalous behavior. Implementing intrusion detection systems, real-time monitoring tools, and security information and event management (SIEM) solutions can aid in proactively identifying and mitigating security threats.
7. Secure Communication Protocols: Choosing secure communication protocols is vital to safeguard sensitive data transmitted between clients and servers. Protocols such as SSL/TLS provide encryption and authentication mechanisms to ensure secure communication channels. However, it’s essential to stay vigilant against emerging security vulnerabilities and adopt updated protocols and cryptographic standards to maintain robust security posture.
Top Client Server Architecture Companies in india
In the dynamic landscape of technology, client-server architecture stands tall as a foundational model enabling seamless interaction between clients and servers, revolutionizing the digital realm. India, a burgeoning hub of technological innovation, boasts a plethora of companies at the forefront of client-server architecture development, propelling businesses towards efficiency and scalability. Let’s delve into the realm of top client-server architecture companies in India, reshaping the digital infrastructure of tomorrow.
-
-
Next Big Technology:

Focus Area
- Mobile App Development
- App Designing (UI/UX)
- Software Development
- Web Development
- AR & VR Development
- Big Data & BI
- Cloud Computing Services
- DevOps
- E-commerce Development
Industries Focus
- Art, Entertainment & Music
- Business Services
- Consumer Products
- Designing
- Education
- Financial & Payments
- Gaming
- Government
- Healthcare & Medical
- Hospitality
- Information Technology
- Legal & Compliance
- Manufacturing
- Media
-
- Infosys: Renowned for its innovative approach to technology, Infosys stands out as a key player in client-server architecture solutions. With a focus on driving digital transformation, Infosys offers a comprehensive suite of services encompassing application modernization, data analytics, and cybersecurity, catering to diverse client needs.
- Wipro: Wipro’s expertise in client-server architecture stems from its deep-rooted experience in delivering end-to-end IT solutions. Through strategic partnerships and a customer-centric approach, Wipro enables businesses to harness the power of client-server architecture for enhanced performance and agility.
- HCL Technologies: With a strong emphasis on innovation and engineering excellence, HCL Technologies delivers bespoke client-server architecture solutions tailored to the unique requirements of businesses. From legacy system modernization to cloud-native application development, HCL empowers organizations to stay ahead in the digital race.
- Tech Mahindra: Tech Mahindra’s proficiency in client-server architecture is evident through its comprehensive service offerings spanning across infrastructure management, application development, and digital transformation. By leveraging emerging technologies such as IoT and AI, Tech Mahindra enables clients to optimize their IT infrastructure for maximum efficiency.
- Persistent Systems: As a niche player in client-server architecture, Persistent Systems excels in providing innovative solutions for complex business challenges. Through its expertise in cloud computing and DevOps practices, Persistent Systems empowers enterprises to build scalable and resilient client-server ecosystems.
- Mindtree: Mindtree’s strategic focus on digital transformation has positioned it as a trusted partner for client-server architecture solutions. With a blend of domain expertise and technological prowess, Mindtree enables organizations to unlock new possibilities through robust and secure client-server deployments.
- L&T Infotech: L&T Infotech combines domain knowledge with technical expertise to deliver best-in-class client-server architecture solutions. Through its customer-centric approach and commitment to innovation, L&T Infotech helps businesses achieve agility and scalability in an ever-evolving digital landscape.
- Cybage: Specializing in niche technology areas, Cybage offers bespoke client-server architecture solutions designed to drive business growth. With a focus on quality and efficiency, Cybage assists clients in harnessing the full potential of client-server architecture for competitive advantage.
- Mphasis: Mphasis leverages its deep domain expertise and global delivery model to deliver cutting-edge client-server architecture solutions. By focusing on digital transformation and innovation, Mphasis enables organizations to stay ahead of the curve in an increasingly digital-centric world.
FAQs On Client Server Architecture
In the realm of computing, client-server architecture stands as a cornerstone concept, facilitating the exchange of data and resources across networks. However, for those new to the world of IT or looking to deepen their understanding, questions often arise. Let’s delve into some frequently asked questions about client-server architecture to shed light on this fundamental framework.
1. What is Client-Server Architecture? At its core, client-server architecture is a model where computational tasks or processes are distributed between clients and servers. Clients, such as computers, smartphones, or other devices, initiate requests for services or resources, while servers, powerful computers or software applications, fulfill these requests by providing the necessary resources or performing the required tasks. This model forms the backbone of modern networked systems and applications.
2. How Does Client-Server Communication Work? Communication between clients and servers occurs via a network, typically using protocols like HTTP, TCP/IP, or FTP. When a client requires a service or resource, it sends a request to the server, specifying the desired action or data. The server processes this request and responds accordingly, providing the requested information or performing the requested task. This communication follows a request-response paradigm, where clients initiate requests and servers respond to them.
3. What Are Some Examples of Client-Server Applications? Client-server architecture is ubiquitous across various domains, powering numerous applications and services that we use daily. Examples include:
- Web Browsing: When you browse the internet, your web browser acts as the client, sending requests to web servers to retrieve web pages.
- Email: Email clients like Outlook or Gmail interact with email servers to send and receive emails.
- Database Management Systems: Applications like MySQL, Oracle, or Microsoft SQL Server serve as servers, managing data and responding to queries from client applications.
4. What Are the Advantages of Client-Server Architecture? Client-server architecture offers several advantages, including:
- Scalability: It allows for easy scalability by adding or upgrading servers to handle increased client demand.
- Centralized Management: Resources and data can be centrally managed on servers, enhancing security and control.
- Resource Sharing: Clients can share resources and access centralized data repositories, promoting collaboration and efficiency.
5. What Are the Challenges or Limitations of Client-Server Architecture?While client-server architecture provides numerous benefits, it also presents some challenges, such as:
- Single Point of Failure: Servers can become single points of failure, leading to system downtime if not properly managed or redundant systems are not in place.
- Network Dependency: Client-server communication relies on network connectivity, making systems susceptible to performance issues or disruptions.
- Security Concerns: Centralized servers can be targeted by malicious attacks, necessitating robust security measures to safeguard data and resources.
6. How Does Client-Server Architecture Compare to Peer-to-Peer (P2P) Architecture? Client-server architecture differs from peer-to-peer (P2P) architecture in several ways. While client-server systems rely on centralized servers to manage resources and facilitate communication, P2P systems distribute tasks and resources among interconnected peers without the need for central coordination. P2P architecture is often associated with file-sharing applications like BitTorrent, where users can directly exchange files with each other.
Thanks for reading our post “Client Server Architecture: Key Components Types Benefits”. Please connect with us to learn more about Best Client Server Architecture.