Manufacturers of cloud computing infrastructure provide their customers with cloud security. However, the onus for ensuring the safety of their information in the cloud is placed on the clients themselves.
Cloud computing relies on the availability of a reliable internet connection. Therefore, data is essential, but internet security is paramount. Unfortunately, there are several entry points for malicious actors to compromise cloud data while accessing it via a black hole.
This highlights the need for cloud security in today’s commercial sector. The cloud service also uses a programme that guarantees the database’s security in the cloud.
You can choose from many service models, such as Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
Table of Contents
Cloud computing categories
Many companies now rely on cloud computing to keep sensitive information safe. The term “cloud computing” can refer to several different services, such as:
Public cloud services
SaaS (Service as a Service), IaaS (Infrastructure as a Service), and PaaS (Platform as a Service) are all examples of public cloud services (Platform as a Service).
Also read : Top 10 Cloud Computing Challenges for IT Service Providers in 2021
Provider of public cloud services also offers private cloud hosting.
A private cloud service is the best choice when you need a secure, isolated cloud environment for your data. The operations of which are handled by an outside organization. One customer at a time can take advantage of this service.
Private cloud services are managed in-house.
They manage the virtual environment themselves at one of the more conventional data centers, and all administrators are in-house.
Services in a hybrid cloud
Cost, security, operations, and access can all benefit from combining private and public cloud computing setups to host applications and data—internal staff and, if necessary, the public cloud service provider will be involved in the operation.
For what reasons is it crucial that cloud infrastructure be protected?
Some of the most compelling arguments for investing in cloud security are outlined here.
- Organizations can use cloud security to protect their data. In the unfortunate event that they lose critical data, they can get it back. Because of this, cloud security is a must for the firm.
- There are multiple entry points for hackers to the database, even if the cloud servers themselves are safe. Furthermore, sensitive information can be viewed or deleted by anyone.
- Your rivals can easily obtain your information and steal your tactics in several ways. Therefore, organizations employ security measures, for example, to keep sensitive information safe from thieves and rivals.
- Trust allows you to keep using cloud storage. In addition, cloud service providers offer security measures to protect user data from unauthorized access.
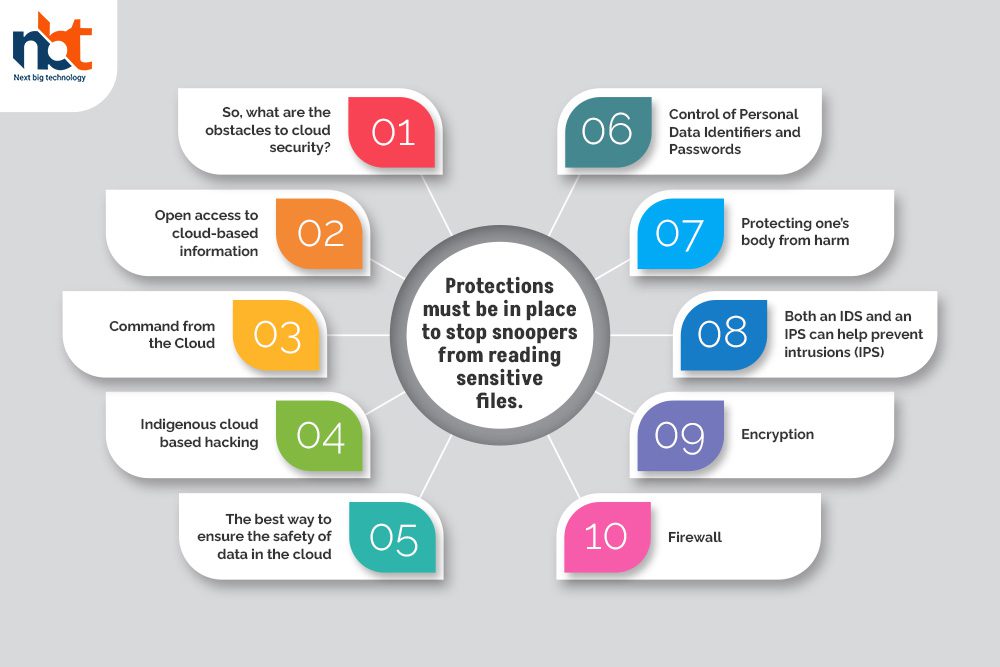
Protections must be in place to stop snoopers from reading sensitive files.
So, what are the obstacles to cloud security?
Many people prefer to save their data in the cloud rather than on their servers. Hence, as a result, the total number of authorized users who can view this data. But, just as every coin has two sides, there are several obstacles the provider must overcome to keep the data safe.
Open access to cloud-based information
Workers can access the information even when not physically in the workplace. There is a risk of information exhaustion when workers process data in a public setting and don’t have access to the corresponding database.
Command from the Cloud
Similarly, organizations might benefit from alternatives that give authorized users access to groups. Therefore, companies risk having their data stolen if they provide questionable individuals access to their databases.
Indigenous cloud-based hacking
Cloud security breaches are distinct from those on-premises since information is frequently stolen using the cloud’s intrinsic features.
The best way to ensure the safety of data in the cloud
The provider may use several techniques to ensure the database’s safety in the cloud. The following are some methods that cloud providers can employ to safeguard their data stores.
Control of Personal Data Identifiers and Passwords
Identity and access management is a powerful tool for protecting databases (IAM). By utilizing IAM, the provider can provide their client with the option of granting several people access to the same database.
Additionally, the client has the capability of monitoring the user’s actions. Accordingly, IAM can be used to spot fraud or other forms of questionable conduct by either the client or the provider. Security for the database is maintained in this manner using the service providers.
Protecting one’s body from harm
The database, analogous to a hard drive, stores all the information in the cloud. Therefore, the provider can keep the hard drive in storage at the facility. But if someone else gets their hands on the hard drive or destroys it, all of the client’s information will be gone forever.
To counteract this, the provider uses various security technologies, including video surveillance, biometric access control, and fire and smoke alarms. This allows the service providers to halt any questionable conduct if their team notices it rapidly.
Both an IDS and an IPS can help prevent intrusions (IPS)
Intrusion prevention and detection systems are the backbones of cloud security. The service provider is alerted instantly if there is an attempt to breach security. You can disable the prevention feature to stop the security system from stopping hackers and saving data.
Also read : What Are the Different Types of Cloud Computing?
Encryption
Hackers can steal information during the transfer process by exploiting several security flaws. That is why encryption technology is employed to ensure the security of data exchanges.
When data is moved from one system to another, it is encrypted with encryption technology. Therefore, cybercriminals don’t have enough time to break the encryption. The outcome is that the encrypted information stolen but later retrieved safely employs another piece of technology. All of this data is encrypted and only accessible by the primary users of the cloud database.
Firewall
The firewall has rapidly become one of the most advanced and commonplace forms of online protection. The modern firewall has several new and useful functions. For example, a conventional firewall will defend against packet filtering, tasteful inspection, proxying, IP blocking, domain name blocking, and port blocking.
The latest generation of firewalls is capable of encrypted traffic analysis, application control, and packet inspection.
Conclusion
Nowadays, more and more people are turning to cloud services. However, the cloud’s accessibility over the internet means that safety measures must be taken. However, if the cloud service manages the security of your data, you don’t have to worry about losing it. This highlights the significance of cloud security. And you may rest assured that the data is secure with the operations team.
Thanks for reading our post “Cloud Security – The Detail Guide to Secure Cloud Computing”, please connect with us for any further inquiry. We are Next Big Technology, a leading web & Mobile Application Development Company. We build high-quality applications to full fill all your business needs.