Table of Contents
Understanding API Documentation: Navigating the complexities
In the realm of technology, where digital interactions are the norm, Application Programming Interfaces (APIs) stand as the silent enablers, powering seamless communication between various software components and systems. However, delving into the world of APIs can be a daunting task, especially when faced with the intricacies of API documentation. This guide aims to unravel the complexities surrounding API documentation, empowering you to navigate through with confidence.
Demystifying API Documentation
API documentation serves as a roadmap for developers, offering insights into how to interact with an API effectively. At its core, it provides detailed instructions on endpoints, request parameters, response formats, authentication methods, and error handling. While each API documentation may vary in structure and format, the underlying goal remains consistent: to facilitate seamless integration and utilization of the API.
Understanding the Components
- Endpoints: These are the entry points to an API, representing specific URLs that correspond to different functionalities or resources. Understanding the purpose and usage of each endpoint is crucial for leveraging the API efficiently.
- Request Parameters: Parameters are the data elements passed along with the API request to modify its behavior or filter results. It’s imperative to grasp the significance of each parameter and how it influences the API response.
- Response Formats: APIs typically return data in various formats such as JSON, XML, or HTML. Familiarizing yourself with the response format enables you to parse and utilize the data effectively within your application.
- Authentication: Many APIs require authentication to access protected resources. API documentation elucidates the authentication mechanisms, be it through API keys, OAuth tokens, or other methods, ensuring secure access to the API.
- Error Handling: Errors are inevitable in any software interaction. API documentation outlines the possible error codes, along with their meanings and suggested troubleshooting steps, aiding developers in diagnosing and resolving issues swiftly.
Navigating the Documentation
- Structured Navigation: API documentation is often organized into logical sections or categories, making it easier to locate relevant information. Utilize the table of contents or navigation bar to jump to specific sections of interest.
- Search Functionality: Most API documentation platforms incorporate search functionality, allowing you to quickly find relevant endpoints, parameters, or concepts. Leveraging the search feature can expedite the documentation exploration process.
- Examples and Tutorials: Many API documentation includes comprehensive examples and tutorials to illustrate usage scenarios and best practices. Leveraging these resources can enhance your understanding and proficiency in working with the API.
Best Practices for Utilization
- Thorough Read-through: Take the time to read the API documentation thoroughly, paying attention to detail. Understanding the nuances of the API upfront can save considerable time and effort in the long run.
- Experimentation and Testing: Don’t hesitate to experiment with the API endpoints and parameters in a sandbox environment. Testing different scenarios allows you to gain hands-on experience and uncover any undocumented behaviors.
- Community and Support: Engage with the developer community or seek support forums provided by the API provider. Collaborating with fellow developers and leveraging community resources can offer valuable insights and solutions to challenges encountered.
Handling Versioning: Dealing with changes and updates
In the dynamic landscape of software development, managing changes and updates is paramount. Version control, also known as source control or revision control, is the cornerstone of this process. It facilitates collaboration among developers, ensures the integrity of codebases, and enables efficient tracking of modifications over time. In this article, we’ll delve into the art of handling versioning, exploring best practices and tools to streamline the process effectively.
Understanding Version Control:
Version control involves tracking alterations to files and directories over time. It allows developers to revert to previous versions, compare changes, and merge modifications seamlessly. The primary objectives of version control include:
- History Tracking: Maintaining a chronological record of changes made to the codebase, including who made the changes and when.
- Collaboration: Facilitating collaboration among team members by providing a centralized platform to share and manage code.
- Risk Mitigation: Minimizing the risk of errors and conflicts by enabling developers to work on isolated branches before integrating changes into the main codebase.
Best Practices for Versioning:
- Use Descriptive Commit Messages: When committing changes, provide clear and concise descriptions of the modifications made. This helps other developers understand the purpose of the changes and facilitates easier troubleshooting in the future.
- Branching Strategy: Adopt a branching strategy that suits your project’s requirements. Common approaches include feature branching, where each new feature is developed on a separate branch, and git flow, a branching model that defines a strict structure for managing feature development and releases.
- Regularly Update and Sync: Ensure that team members regularly pull changes from the central repository to stay up-to-date with the latest developments. This minimizes conflicts and ensures that everyone is working on the most recent version of the codebase.
- Code Reviews: Implement a code review process to maintain code quality and catch potential issues early on. Code reviews provide an opportunity for knowledge sharing and help spread best practices across the team.
- Automated Testing: Integrate automated testing into your version control workflow to validate changes automatically. This includes unit tests, integration tests, and continuous integration (CI) pipelines, which run tests whenever new code is pushed to the repository.
Tools for Effective Version Control:
- Git: Git is the most widely used version control system, renowned for its speed, flexibility, and distributed nature. It provides a rich set of features for branching, merging, and managing code repositories.
- GitHub: GitHub is a popular platform for hosting Git repositories and collaborating on software projects. It offers additional features such as issue tracking, pull requests, and project management tools, making it an invaluable resource for teams of all sizes.
- Bitbucket: Bitbucket is another Git repository hosting service that provides similar features to GitHub. It offers seamless integration with other Atlassian products such as Jira and Bamboo, making it an excellent choice for teams using the Atlassian ecosystem.
- GitLab: GitLab is a complete DevOps platform built on top of Git. In addition to version control, it offers features such as CI/CD pipelines, issue tracking, and Kubernetes integration, providing a comprehensive solution for software development and deployment.
Authentication and Authorization: Security hurdles in API usage
In today’s digital landscape, where interconnectedness reigns supreme, Application Programming Interfaces (APIs) serve as the backbone of seamless data exchange between applications. However, amid the convenience and efficiency they offer, ensuring robust security measures is paramount, particularly concerning authentication and authorization.
Authentication and authorization are two fundamental pillars of API security, working hand in hand to safeguard sensitive data and resources from unauthorized access. Let’s delve into the challenges associated with these aspects and explore strategies to overcome them effectively.
Understanding Authentication:
Authentication is the process of verifying the identity of a user or application attempting to access an API. Traditional methods like API keys and basic authentication have their shortcomings, such as susceptibility to interception and replay attacks. Additionally, managing and securing a plethora of API keys can be daunting, especially in large-scale applications.
To mitigate these challenges, modern authentication mechanisms like OAuth 2.0 and JSON Web Tokens (JWT) have gained prominence. OAuth 2.0 facilitates secure authorization by enabling delegated access, while JWT provides a compact and self-contained way to transmit authentication credentials. However, implementing these protocols requires meticulous configuration and adherence to best practices to prevent vulnerabilities like token leakage and injection attacks.
Addressing Authorization Challenges:
Authorization determines what actions a user or application can perform within an API based on their authenticated identity and assigned privileges. Role-based access control (RBAC) and attribute-based access control (ABAC) are common authorization models employed to enforce granular access policies. Nevertheless, configuring and managing access control lists (ACLs) can be complex, especially in dynamic environments where permissions evolve frequently.
To streamline authorization processes, employing policy enforcement points (PEPs) and policy decision points (PDPs) can automate access control enforcement based on predefined rules and conditions. Implementing fine-grained access control ensures that only authorized entities can access specific resources or perform designated operations, bolstering overall API security.
Overcoming Security Hurdles:
Despite the advancements in authentication and authorization mechanisms, several challenges persist in securing API usage:
- Insufficient Token Management: Improper handling and storage of authentication tokens can lead to security vulnerabilities like token leakage and man-in-the-middle attacks. Implementing token rotation, encryption, and stringent access token lifetimes can mitigate these risks.
- Inadequate Logging and Monitoring: Without comprehensive logging and real-time monitoring capabilities, detecting and responding to security incidents becomes arduous. Leveraging robust logging frameworks and intrusion detection systems (IDS) enables proactive threat detection and incident response.
- API Versioning and Compatibility: Managing multiple API versions while ensuring backward compatibility introduces complexities in maintaining consistent security measures across different iterations. Employing versioning strategies like semantic versioning and API gateways can streamline version management and ensure uniform security protocols.
- Third-Party Integration Risks: Integrating third-party APIs introduces inherent security risks, as it involves trusting external entities with access to sensitive data. Performing thorough vendor assessments, enforcing secure communication protocols, and implementing data encryption can mitigate the risks associated with third-party integrations.
Rate Limiting and Quotas: Managing usage restrictions
In today’s digitally driven world, where the demand for online services is ever-increasing, managing usage restrictions has become paramount for businesses. Rate limiting and quotas emerge as indispensable tools in this endeavor, allowing organizations to maintain service quality, prevent abuse, and optimize resource allocation. Let’s delve deeper into these concepts and explore how they can be effectively managed.
Understanding Rate Limiting and Quotas:
Rate limiting involves controlling the number of requests a client can make to a server within a specified timeframe. This mechanism prevents systems from being overwhelmed by excessive traffic, ensuring smooth operation for all users. Quotas, on the other hand, set limits on the total amount of resources or data that a client can consume over a given period. They serve as a means of resource allocation and cost control, safeguarding against misuse and ensuring fair access for all users.
Benefits of Rate Limiting and Quotas:
Implementing rate limiting and quotas offers several benefits for both service providers and users:
- Enhanced Performance: By regulating the flow of requests, rate limiting prevents server overload, minimizing latency, and ensuring consistent performance for users.
- Improved Security: Rate limiting acts as a deterrent against malicious activities such as DDoS attacks and brute force login attempts, safeguarding system integrity and user data.
- Resource Optimization: Quotas help optimize resource allocation by allocating resources based on user needs and priorities, thereby maximizing efficiency and cost-effectiveness.
- Fair Usage: Quotas ensure fair access to resources for all users by preventing individuals or entities from monopolizing resources, promoting equitable usage across the board.
Effective Management Strategies:
To leverage the full potential of rate limiting and quotas, organizations must adopt effective management strategies:
- Set Realistic Limits: Establishing appropriate limits requires a careful balance between preventing abuse and accommodating legitimate usage. Analyze past usage patterns and user behavior to set realistic limits that meet the needs of your user base.
- Monitor and Adjust: Regularly monitor system usage and performance metrics to identify any anomalies or bottlenecks. Adjust rate limits and quotas dynamically based on traffic patterns and resource availability to ensure optimal performance.
- Prioritize Critical Services: Identify critical services or APIs that require priority access and allocate resources accordingly. Implement tiered quotas to differentiate between essential and non-essential functionalities, ensuring uninterrupted service for mission-critical operations.
- Communicate Transparently: Transparent communication is key to managing user expectations and fostering trust. Clearly articulate usage restrictions, including rate limits and quotas, in your service agreements and documentation. Provide users with visibility into their usage metrics and notifications when they approach or exceed their limits.
- Implement Scalable Solutions: As your user base grows and usage patterns evolve, scalability becomes crucial. Implement scalable rate limiting and quota management solutions that can accommodate increasing demand without compromising performance or user experience.
Data Formatting and Parsing: Ensuring compatibility and accuracy
In the ever-expanding realm of data management, one crucial aspect stands out: formatting and parsing. These twin processes are the bedrock of ensuring data compatibility and accuracy across various platforms, systems, and applications. Whether you’re a seasoned data scientist, a software engineer, or a business analyst, understanding the nuances of data formatting and parsing is paramount for efficient and effective data utilization.
Understanding Data Formatting
Data formatting refers to the process of structuring raw data into a predefined layout or pattern. This transformation makes data readable and interpretable by both humans and machines. It involves organizing data in a consistent manner, typically adhering to specific standards or protocols. The goal is to facilitate seamless data exchange and interpretation.
Importance of Data Formatting
- Interoperability: Standardized data formats enable interoperability between different systems and applications. For instance, XML, JSON, CSV, and YAML are widely used formats that promote data exchange and integration across diverse platforms.
- Clarity and Readability: Well-formatted data is easier to comprehend and manipulate. Clear formatting conventions enhance data readability, reducing the likelihood of errors during processing.
- Consistency: Consistent formatting simplifies data management and analysis. It streamlines workflows and promotes uniformity across datasets, enhancing overall data quality.
The Significance of Data Parsing
Data parsing complements formatting by extracting relevant information from formatted data structures. Parsing involves breaking down raw data into its constituent parts and interpreting their meanings. This process is indispensable for extracting actionable insights and facilitating decision-making.
Key Aspects of Data Parsing
- Syntax Analysis: Parsing entails analyzing the syntactic structure of data to identify meaningful elements. This involves recognizing patterns, delimiters, and markers that delineate different data components.
- Data Validation: Parsing often includes data validation to ensure integrity and accuracy. Validating parsed data against predefined rules helps identify discrepancies or anomalies that may compromise data quality.
- Error Handling: Effective parsing strategies incorporate robust error handling mechanisms to address unexpected data formats or errors gracefully. Error detection and recovery mechanisms mitigate the risk of processing failures and data corruption.
Ensuring Compatibility and Accuracy
Achieving compatibility and accuracy in data formatting and parsing requires a systematic approach and adherence to best practices.
Best Practices:
- Standardization: Adhere to established data formatting standards and conventions such as XML, JSON, or CSV to promote compatibility and interoperability.
- Robust Parsing Algorithms: Utilize robust parsing algorithms capable of handling diverse data formats and structures effectively. Consider employing libraries or frameworks specifically designed for parsing tasks.
- Data Validation: Implement comprehensive data validation routines to verify the integrity and accuracy of parsed data. Perform sanity checks and boundary validations to detect and mitigate errors.
- Error Handling: Develop robust error handling mechanisms to gracefully handle parsing errors and exceptions. Incorporate logging and notification mechanisms to facilitate troubleshooting and debugging.
- Testing and Validation: Thoroughly test data formatting and parsing workflows using diverse datasets and edge cases. Conduct validation tests to verify data accuracy, completeness, and conformance to specifications.
Error Handling: Strategies for effective troubleshooting
In the realm of software development, errors are an inevitable part of the process. Whether you’re a seasoned developer or just starting out, encountering errors and knowing how to effectively troubleshoot them is crucial for ensuring smooth operations and delivering high-quality products. In this article, we’ll delve into the world of error handling and explore strategies for efficient troubleshooting.
Understanding Errors:
Before delving into strategies for handling errors, it’s essential to understand the types of errors that can occur. Errors in software development can range from syntax errors and runtime errors to logical errors. Each type requires a different approach for effective resolution.
- Syntax Errors: These errors occur when the code violates the syntax rules of the programming language. They are usually identified by the compiler or interpreter during the compilation or execution phase.
- Runtime Errors: Runtime errors occur during the execution of the program and are often caused by issues such as division by zero, out-of-bounds array access, or invalid input.
- Logical Errors: Logical errors, also known as bugs, occur when the program produces unexpected results due to flaws in the algorithm or logic of the code.
Strategies for Effective Error Handling:
- Logging and Monitoring: Implement robust logging mechanisms to capture relevant information about errors. Logging can provide insights into the context in which errors occur, making it easier to diagnose and troubleshoot issues. Additionally, monitoring systems can alert developers to potential errors in real-time, allowing for proactive resolution.
- Graceful Error Handling: Design your application to handle errors gracefully. Instead of crashing the entire program, implement error handling mechanisms to gracefully recover from errors and maintain application stability. This may involve displaying user-friendly error messages, logging the error details, and providing alternative paths for users to continue their workflow.
- Testing and Debugging: Thorough testing and debugging are essential for identifying and resolving errors early in the development process. Adopt a systematic approach to testing, including unit tests, integration tests, and regression tests, to uncover potential issues before they manifest in production environments. Utilize debugging tools and techniques to trace the root cause of errors and validate fixes.
- Error Recovery and Retry Mechanisms: Implement error recovery mechanisms to automatically recover from transient errors without manual intervention. This may involve retrying failed operations, implementing exponential backoff strategies, or failing over to alternative resources or services. By automating error recovery, you can minimize downtime and improve the resilience of your application.
- Error Analysis and Root Cause Investigation: Invest time in analyzing errors and investigating their root causes. Use data-driven approaches such as error analytics and performance monitoring to identify patterns and trends in error occurrences. Conduct thorough root cause analysis to understand the underlying factors contributing to errors and implement preventative measures to mitigate future occurrences.
- Continuous Improvement: Error handling is an ongoing process that requires continuous improvement. Solicit feedback from users and stakeholders to identify areas for enhancement and prioritize error resolution based on impact and severity. Regularly review and refine your error handling strategies to adapt to evolving requirements and challenges.
Performance Optimization: Enhancing speed and efficiency
In today’s fast-paced digital world, where every millisecond counts, ensuring your website, application, or system operates at peak performance is paramount. Performance optimization isn’t just about making things faster; it’s about enhancing speed and efficiency to deliver a seamless user experience while maximizing resources. In this guide, we’ll delve into the strategies and techniques you can employ to unlock the full potential of your digital assets.
Understanding Performance Optimization: Performance optimization is the process of fine-tuning various aspects of your system to achieve better responsiveness, faster load times, and overall efficiency. It encompasses a range of factors, including code optimization, server configuration, network optimization, and resource management.
Identifying Performance Bottlenecks: The first step in optimizing performance is to identify the bottlenecks that are slowing down your system. This could be inefficient code, excessive server requests, bulky assets, database queries, or network latency. Utilize tools like profiling, monitoring, and analytics to pinpoint areas for improvement.
Streamlining Code and Algorithms: Optimizing code and algorithms is crucial for improving the speed and efficiency of your system. This involves writing clean, efficient code, minimizing unnecessary operations, and utilizing data structures and algorithms optimized for performance. Regular code reviews and refactoring can help identify and eliminate bottlenecks.
Leveraging Caching Mechanisms: Caching is a powerful technique for reducing load times and server load by storing frequently accessed data in temporary storage. Implement caching mechanisms at various levels, including browser caching, server-side caching, and database caching, to serve content faster and reduce the need for redundant processing.
Optimizing Server and Network Resources: Server configuration and network optimization play a significant role in overall performance. Fine-tune server settings, such as memory allocation, thread pools, and connection limits, to handle incoming requests efficiently. Implement content delivery networks (CDNs) and optimize network protocols to reduce latency and speed up data transmission.
Managing Resources Effectively: Resource management is essential for maintaining optimal performance under varying loads. Implement techniques like load balancing, scalability, and resource pooling to distribute workloads evenly across servers and prevent resource contention. Monitor resource usage regularly and scale infrastructure dynamically to accommodate changing demand.
Dependency Management: Dealing with interconnected APIs
In the ever-expanding landscape of software development, dependency management stands as a crucial pillar. At the heart of this practice lies the intricate web of interconnected APIs (Application Programming Interfaces), each serving as a vital conduit for data exchange and functionality integration. In this article, we delve into the nuances of dependency management, exploring strategies to navigate and optimize the utilization of interconnected APIs effectively.
Understanding the Dependency Web
In contemporary software development, applications rarely operate in isolation. Instead, they rely on a myriad of external services and libraries, often accessed via APIs. These APIs act as gateways, facilitating seamless communication between disparate systems and enabling developers to leverage functionalities without reinventing the wheel.
However, this interconnectedness introduces a layer of complexity in managing dependencies. A change or disruption in one API can potentially cascade across multiple interconnected components, leading to compatibility issues, downtime, or even system failures. Thus, adeptly managing these dependencies becomes paramount for ensuring the reliability and robustness of software systems.
Challenges in Dependency Management
The proliferation of APIs poses several challenges for developers:
- Version Compatibility: Different versions of APIs may introduce changes in functionality or data formats, necessitating careful version management to ensure compatibility across interconnected components.
- Dependency Conflicts: Integrating multiple APIs may result in conflicts between dependencies, where one API relies on a different version of a shared library than another, leading to runtime errors or unexpected behaviors.
- Reliability and Stability: Relying on external APIs introduces dependencies on third-party services, making the application vulnerable to service outages, downtime, or changes in API behavior.
- Security Concerns: Integrating external APIs requires handling sensitive data, raising security concerns such as data privacy, authentication, and authorization.
Strategies for Effective Dependency Management
To mitigate these challenges and navigate the web of dependencies successfully, developers can adopt the following strategies:
- Dependency Versioning: Employ semantic versioning and dependency lock files to manage and track API versions rigorously, ensuring consistent behavior across environments.
- Isolation and Modularity: Encapsulate API interactions within modular components, minimizing dependencies and facilitating easier maintenance and updates.
- Monitoring and Fault Tolerance: Implement robust monitoring and error handling mechanisms to detect and gracefully handle failures in external API dependencies, ensuring the resilience of the overall system.
- Fallback Mechanisms: Implement fallback mechanisms or alternative paths for critical functionalities, enabling the application to gracefully degrade in the face of API failures or disruptions.
- Security Best Practices: Adhere to security best practices such as encryption, authentication, and rate limiting to safeguard data integrity and mitigate security risks associated with external API integrations.
- Documentation and Communication: Maintain comprehensive documentation outlining API usage, dependencies, and integration guidelines, fostering clear communication among development teams and stakeholders.
API Lifecycle Management: Balancing maintenance and development
In the realm of modern software development, Application Programming Interfaces (APIs) have become the backbone of connectivity, enabling seamless interaction between diverse systems and applications. However, the journey of an API from inception to retirement is not a one-time affair but a continuous lifecycle marked by various stages, including creation, deployment, maintenance, and eventual decommissioning. In this dynamic process, striking a delicate balance between maintenance and development is paramount to ensure the efficiency, reliability, and longevity of APIs.
Understanding the API Lifecycle:
The API lifecycle encompasses several distinct phases, each demanding meticulous attention and strategic planning:
- Design: This initial phase lays the foundation for the API, defining its purpose, functionality, and structure. Here, developers must carefully consider factors like usability, scalability, and security to ensure the API meets the needs of its intended users.
- Development: With the design blueprint in hand, developers embark on the implementation phase, where they write code, integrate necessary features, and conduct thorough testing to ensure the API functions as intended. Agile methodologies often govern this stage, allowing for iterative improvements and quick adaptation to changing requirements.
- Deployment: Once developed, the API is deployed to production environments, making it accessible to consumers. Effective deployment strategies, such as versioning and environment management, play a crucial role in ensuring smooth transitions and minimizing disruptions for end-users.
- Maintenance: The maintenance phase represents the longest and most critical stage of the API lifecycle. Here, developers address bugs, implement enhancements, and manage evolving dependencies to uphold the API’s performance, security, and compatibility. Proactive monitoring and regular updates are essential to preemptively identify and resolve potential issues before they impact users.
- Decommissioning: As technology evolves and business priorities shift, some APIs may outlive their usefulness or become obsolete. The decommissioning phase involves gracefully retiring outdated APIs, migrating users to newer alternatives, and mitigating any associated risks or disruptions.
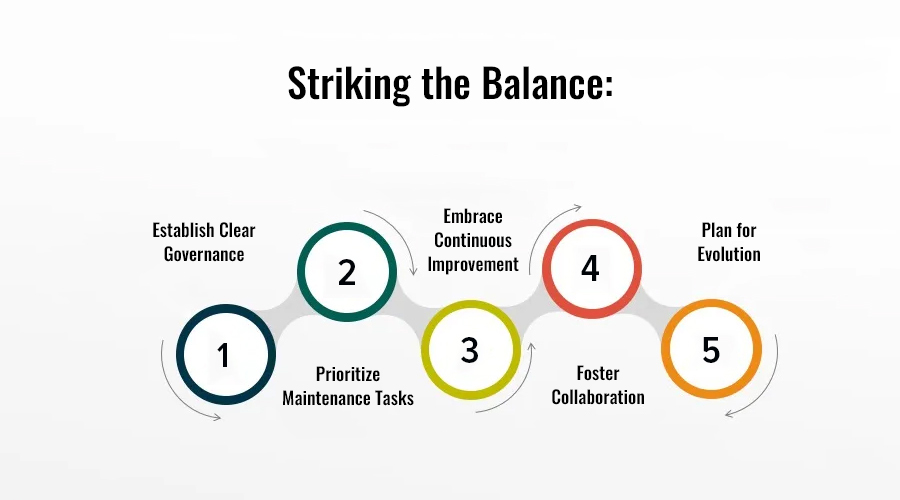
Striking the Balance:
Achieving harmony between API maintenance and development requires a strategic approach that prioritizes both short-term stability and long-term innovation. Here are some key considerations to help strike this balance effectively:
- Establish Clear Governance: Define robust governance policies and procedures to govern the entire API lifecycle, including version control, documentation standards, and change management protocols. Clear guidelines empower developers to make informed decisions while ensuring consistency and compliance across the organization.
- Prioritize Maintenance Tasks: Regularly assess the health and performance of APIs to identify areas requiring maintenance or optimization. Prioritize tasks based on their impact on user experience, security vulnerabilities, and business priorities. Implement automated monitoring and alerting systems to detect issues proactively and streamline maintenance efforts.
- Embrace Continuous Improvement: Cultivate a culture of continuous improvement within your development team, encouraging experimentation, feedback, and knowledge sharing. Embrace DevOps practices to automate repetitive tasks, streamline workflows, and accelerate the delivery of enhancements and bug fixes without sacrificing stability.
- Foster Collaboration: Foster collaboration between development, operations, and business stakeholders to align API initiatives with organizational goals and customer needs. Regular communication and feedback loops facilitate transparency, identify emerging requirements, and ensure that maintenance efforts are aligned with strategic objectives.
- Plan for Evolution: Anticipate future scalability and evolution requirements during the initial design phase to minimize technical debt and facilitate seamless transitions between development and maintenance activities. Embrace scalable architectures, microservices, and API management platforms to adapt to changing business dynamics and technological landscapes.
Top Challenges of Working with APIs Development Companies
In today’s digitally-driven world, Application Programming Interfaces (APIs) are the linchpin of connectivity and functionality for countless applications and services. They enable seamless integration and communication between disparate systems, unlocking a world of possibilities for businesses. However, while APIs offer immense potential, collaborating with API development companies comes with its own set of challenges. Let’s delve into some of the top hurdles that organizations may encounter in this process.
-
-
Next Big Technology:

Focus Area
- Mobile App Development
- App Designing (UI/UX)
- Software Development
- Web Development
- AR & VR Development
- Big Data & BI
- Cloud Computing Services
- DevOps
- E-commerce Development
Industries Focus
- Art, Entertainment & Music
- Business Services
- Consumer Products
- Designing
- Education
- Financial & Payments
- Gaming
- Government
- Healthcare & Medical
- Hospitality
- Information Technology
- Legal & Compliance
- Manufacturing
- Media
-
- Misaligned Expectations: Misunderstandings regarding project scope, timelines, and deliverables often arise when expectations are not clearly defined from the outset. API development projects can be complex, and discrepancies in understanding can lead to frustration and delays. To mitigate this challenge, it’s crucial to establish a comprehensive project plan with well-defined goals, milestones, and success criteria.
- Quality Assurance: Ensuring the reliability, security, and performance of APIs is paramount, yet quality assurance can pose significant challenges. Testing APIs thoroughly across various use cases, platforms, and devices requires meticulous planning and execution. Moreover, maintaining consistency and compatibility with evolving technologies and standards adds another layer of complexity to the QA process.
- Scalability and Flexibility: As businesses grow and evolve, their API requirements may change, necessitating scalability and flexibility in the solutions provided by API development companies. Building APIs that can accommodate future expansion while maintaining backward compatibility requires careful architectural design and strategic planning. Failure to anticipate scalability needs can result in costly rework down the line.
- Security Concerns: Security breaches and data vulnerabilities pose serious risks to both businesses and their customers. Collaborating with API development companies requires a robust approach to security throughout the development lifecycle. From implementing encryption protocols and access controls to conducting regular security audits and updates, prioritizing security is non-negotiable in today’s threat landscape.
- Integration Complexity: Integrating APIs with existing systems and third-party services can be a complex undertaking, particularly in heterogeneous IT environments. Compatibility issues, data format discrepancies, and dependency management challenges may arise, complicating the integration process. Thorough testing and documentation, along with proactive support from API developers, can help streamline integration efforts.
- Cost Management: Budget constraints and cost overruns are common challenges faced by organizations embarking on API development projects. Balancing the need for quality and innovation with financial considerations requires careful budgeting and resource allocation. API development companies must provide transparent pricing models and cost estimates upfront, enabling businesses to make informed decisions and avoid financial surprises.
FAQs On Challenges of Working with APIs
In today’s interconnected digital landscape, Application Programming Interfaces (APIs) serve as the backbone of modern software development, enabling seamless communication and data exchange between different applications and systems. However, despite their undeniable benefits, working with APIs presents its own set of challenges. Let’s delve into some frequently asked questions regarding these challenges:
1. What are the common challenges encountered when working with APIs? Working with APIs can pose several challenges, including:
- Security Concerns: Ensuring the security of data transmitted via APIs is paramount. Vulnerabilities such as unauthorized access, data breaches, and injection attacks must be addressed.
- Compatibility Issues: Integrating APIs across different platforms and versions can lead to compatibility issues, requiring careful planning and testing.
- Reliability and Performance: API reliability and performance can fluctuate, leading to downtime, latency issues, and degraded user experiences.
- Documentation and Support: Inadequate documentation and lack of robust support can hinder developers’ ability to effectively utilize APIs.
- Rate Limiting and Throttling: APIs often impose rate limits and throttling mechanisms to manage traffic, which can impact application functionality and user experience.
2. How can security concerns associated with APIs be mitigated? To mitigate security concerns, developers should implement robust authentication mechanisms such as OAuth or API keys, encrypt sensitive data during transmission using HTTPS, and employ techniques like input validation and output encoding to prevent injection attacks. Regular security audits and penetration testing can also help identify and address vulnerabilities proactively.
3. What strategies can be adopted to address compatibility issues with APIs? Adopting standardized protocols like REST or GraphQL can enhance interoperability between different systems. Additionally, versioning APIs, maintaining backward compatibility, and employing comprehensive testing methodologies across various environments can help identify and resolve compatibility issues early in the development lifecycle.
4. How can developers ensure the reliability and performance of APIs? Developers can ensure API reliability and performance by implementing effective error handling mechanisms, monitoring API usage and performance metrics, employing caching strategies to reduce latency, and leveraging content delivery networks (CDNs) for optimized content delivery. Load testing and scalability planning are also essential to anticipate and address performance bottlenecks.
5. What steps should developers take to improve API documentation and support? Developers should prioritize clear and comprehensive API documentation, including usage examples, error codes, and troubleshooting guidelines. Additionally, establishing dedicated support channels, such as forums, ticketing systems, or developer portals, can facilitate timely assistance and foster a supportive developer community.
6. How can developers manage rate limiting and throttling challenges effectively? Developers can mitigate rate limiting and throttling challenges by implementing adaptive throttling mechanisms based on API usage patterns, optimizing API requests to minimize unnecessary calls, and utilizing caching mechanisms to reduce the frequency of repetitive requests. Effective communication of rate limits and proactive monitoring can also help manage user expectations and mitigate disruptions.
Thanks for reading our post “Challenges of Working with APIs from Developers’ Perspective”. Please connect with us to learn more about Best Challenges of Working with APIs.