Node.js is a runtime environment for JavaScript, which means it has everything you need to run a JavaScript programme. Even though Node.js has strong security built in, you still need to take steps to protect your applications.
Table of Contents
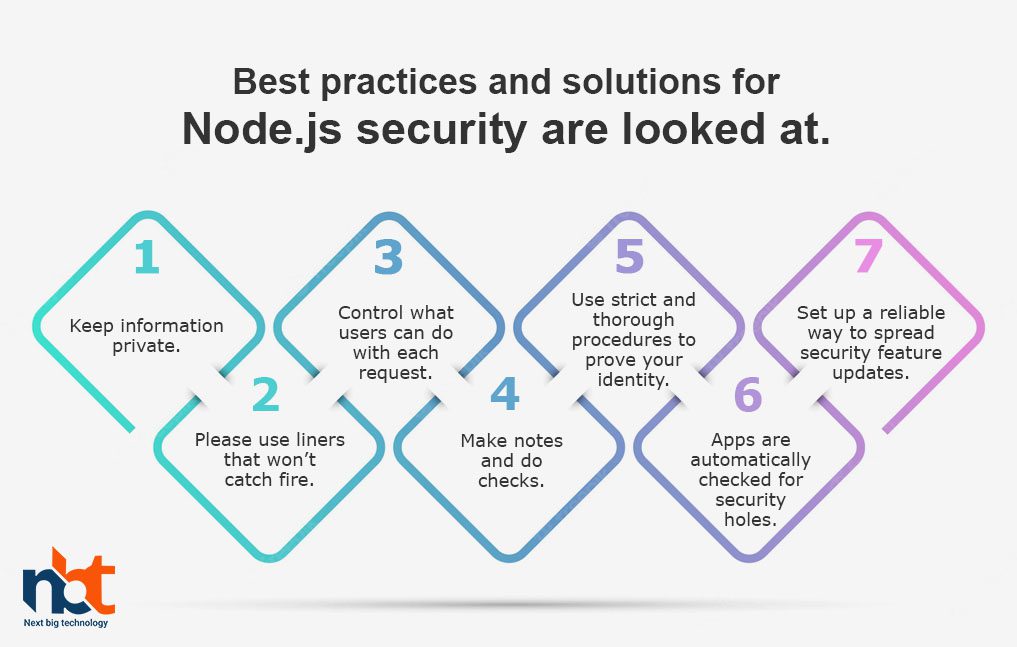
Best practices and solutions for Node.js security are looked at.
Here is a complete list of tips for making sure that applications built with the node.js framework are safe:
Keep information private.
Put only some of your hopes in the beginning. Think about the message you want to send as well. You can easily send all the data for a certain object to the foreground and filter it to control the information shown there. On the other hand, hackers can easily find any secret information sent from the server.
Solution
Please give only the necessary information. From a database, it’s easy to get both first and last names. Your level of effort might go up. But there is no doubt that the price is fair.
Please use liners that won’t catch fire.
Vulnerability scans can be done by hand or by a machine. Also, you can still find common vulnerabilities even if you are programming.
Solution
Install a linter plugin, like eslint-plugin-security. When insecure ways of coding are used, this kind of warning is sent out.
Also Read : Reasons To Choose NodeJS for Web App Development
Control what users can do with each request
It’s mostly about making sure the programme works the way it should. You can limit a user’s access to certain URLs or parts of your app based on their role in the system.
Solution
The best way to get rid of this sensitivity is to test app modules that depend on certain user rights by hand. It’s better to put middleware and rules for access control on the server.
This makes it harder for JWT (JSON Web Token) authorization tokens or cookies to be used for client-side access management. Controls must be established for who can look at logs and how much data can be pulled from APIs. This lets administrators know when serious steps must be taken to stop more attacks and failures.
Make notes and do checks.
Auditing and logging are also linked to secure node.js. The end goal is to make a security system from scratch, but this takes a lot of work that must be recorded and evaluated.
Solution
Some hackers want to make your app useless, which can be found even without recording, but others want to stay anonymous as long as possible. Logs and metrics can help in this situation by showing any differences.
The bare-bones recording will teach you less. There are many ways to talk to and interact with the outside world if your apps, hackers, or third-party APIs send you strange requests. We can add a specific layer to your system’s security to strengthen it.
It’s important to evaluate your app’s risks and weaknesses and find out what they are. There is room for different routines that only work in certain situations to be built into the system. Logging and monitoring make it possible to keep track of everything that happens in the programme. So, monitoring is a way to let you know if a security hole is found by making a sound.
Use strict and thorough procedures to prove your identity.
A common flaw is an authentication scheme that doesn’t work or doesn’t work at all. This could happen because many developers think they are safe, but it is easy to attack unstable or weak authentication.
Solution
If you’re having trouble logging in with Node.js, switching to a more modern authentication method is one way to fix it. Don’t use the cryptographic libraries with Node.js to make a password. Instead, use Scrypt or Bcrypt. Make sure to limit failed attempts to log in. Always tell the user that they entered their login or password correctly.
A good policy for managing sessions is also important. Use authentication with two factors. App security can be made much better if the right steps are taken. Modules like Speakeasy or node-2fa can help you do this.
Apps are automatically checked for security holes.
Some libraries and modules make up the Node.js ecosystem. Because of this, there could be a security risk. You can’t be sure it is safe if you use a code made by someone else.
Solution
To fix this problem, automated vulnerability scans need to be run regularly. So, you can find out which dependencies have a certain weakness. You can also choose NPM analysis for important monitoring.
Set up a reliable way to spread security feature updates.
A website or app can be attacked if it doesn’t have the right protections or doesn’t have enough of them. The wrong settings can also cause security holes. It makes App containers, databases, servers, and other parts of the app stack more vulnerable to attack.
Solution
You should make credentials and permissions the same in every context. Hackers can easily take advantage of Node.js applications by using aggressive dictionary attacks on login forms that are protected by default package settings and user account passwords. But bad people can use the settings that come with a package.
Also Read : Looking For Top NodeJS Development Agency: Why Hire NBT?
Why does the history of the Node.Js project pose a security risk?
There are no security or licensing issues that open-source components pass on to open-source programmes. The problem is that the tools for finding vulnerabilities in open-source software, like dynamic and static code analysis, need to improve.
To find open-source Node.js modules, you must look at the package manager index file that lists the requirements. But the index file has no open-source parts that have been used again.
The open-source community often reuses old projects to speed up development. Cut down on development times and get the most out of integrating functionality.
This lets programmers working on closed-source and open-source projects add new features and methods to existing files. Because of this, many Node.js projects have their license terms in addition to those of Node.js.
Conclusion
Threats to a company’s security can cause losses of tens of thousands of dollars over time. Even though the breach caused much money to be lost, you can’t just price sensitive information based on how much of it got out. Not every bad attempt to stop our app from working can be stopped. Still, we can be sure that, at worst, the effects of our irresponsibility will be small.
Thanks for reading our post “Best Practices To Secure Node JS Applications”, please connect with us for any further inquiry. We are Next Big Technology, a leading web & Mobile Application Development Company. We build high-quality applications to full fill all your business needs.